A system administrator receives a warning that their DPE I/O Module has a fault. In this situation, which type of replacement is required?
Correct Answer:C
Your storage system is designed to be powered on continuously. Most components are hot swappable; that is, you can replace or install these components while the storage system is running.
What is required for file system creation on Unity?
Correct Answer:D
References:
https://www.dellemc.com/en-us/documentation/unity-family/unity-p-configure-nfs-file-sharing/03-unity-nfs-c-c
What is used to create a Proxy NAS Server on a Dell EMC Unity array?
Correct Answer:D
What is the correct order of steps to attach a snapshot to a host?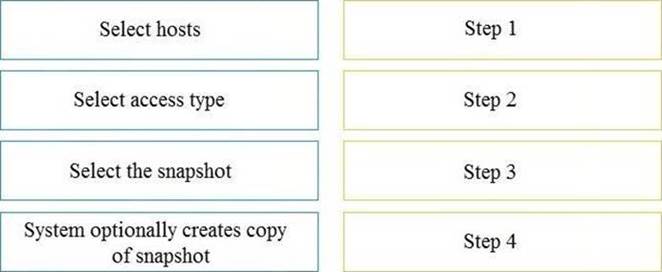
Solution: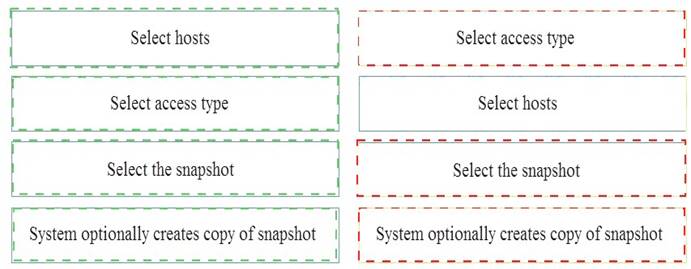
Does this meet the goal?
Correct Answer:A
How is encryption set for a Unity storage system?
Correct Answer:D
D@RE is included by default on Unity arrays and included in the Unity license file unless otherwise requested during ordering. Therefore, all that is needed to activate D@RE is to install the D@RE enabled license file. The license installation process is not specific to D@RE, and is required to be performed before using the array. When logging into Unisphere for the first time, license installation appears as a step of the Unisphere Configuration Wizard, prompting the administrator to install the license file obtained from EMC. If this license file includes D@RE functionality, D@RE will be enabled once the license file is installed successfully
Note: Unity storage systems address sensitive data concerns through controller-based Data at Rest Encryption
(D@RE), which encrypts stored data as it is written to disk.
D@RE is a license controlled feature available by default on Unity storage systems, and, being designed to be largely invisible to administrative end users, requires almost no effort to enable or manage. Enabling the feature or backing up the encryption keys externally takes just seconds, and redundant keystore backups stored on array ensure that user data is always as available as it is secure.