George is the network administrator of a large Internet company on the west coast. Per corporate policy, none of the employees in the company are allowed to use FTP or SFTP programs without obtaining approval from the IT department. Few managers are using SFTP program on their computers.
Before talking to his boss, George wants to have some proof of their activity. George wants to use Ethereal t monitor network traffic, but only SFTP traffic to and from his network. What filter should George use in Ethereal?
Correct Answer:C
How many bits is Source Port Number in TCP Header packet?
Correct Answer:D
The Web parameter tampering attack is based on the manipulation of parameters exchanged between client and server in order to modify application data, such as user credentials and permissions, price and quantity of products, etc.
Usually, this information is stored in cookies, hidden form fields, or URL Query Strings, and is used to increase application functionality and control. This attack takes advantage of the fact that many programmers rely on hidden or fixed fields (such as a hidden tag in a form or a parameter in a URL) as the only security measure for certain operations.
Attackers can easily modify these parameters to bypass the security mechanisms that rely on them.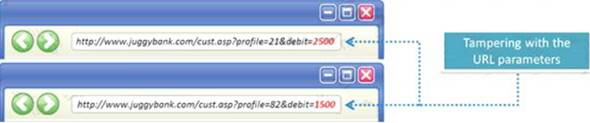
What is the best way to protect web applications from parameter tampering attacks?
Correct Answer:D
Which one of the following is a command line tool used for capturing data from the live network and copying those packets to a file?
Correct Answer:D
Which of the following is NOT related to the Internal Security Assessment penetration testing strategy?
Correct Answer:B