Identify the attack represented in the diagram below: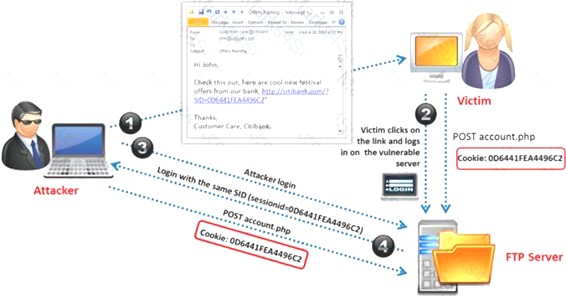
Correct Answer:B
After attending a CEH security seminar, you make a list of changes you would like to perform on your
network to increase its security. One of the first things you change is to switch the Restrict Anonymous setting from 0 to 1 on your servers. This, as you were told, would prevent anonymous users from establishing a null session on the server.
Using User info tool mentioned at the seminar, you succeed in establishing a null session with one of the servers. Why is that?
Correct Answer:A
Which of the following are the default ports used by NetBIOS service?
Correct Answer:A
In which of the following IDS evasion techniques does IDS reject the packets that an end system accepts?
Correct Answer:D
Which of the following is developed to address security concerns on time and reduce the misuse or threat of attacks in an organization?
Correct Answer:A