Refer to the exhibits.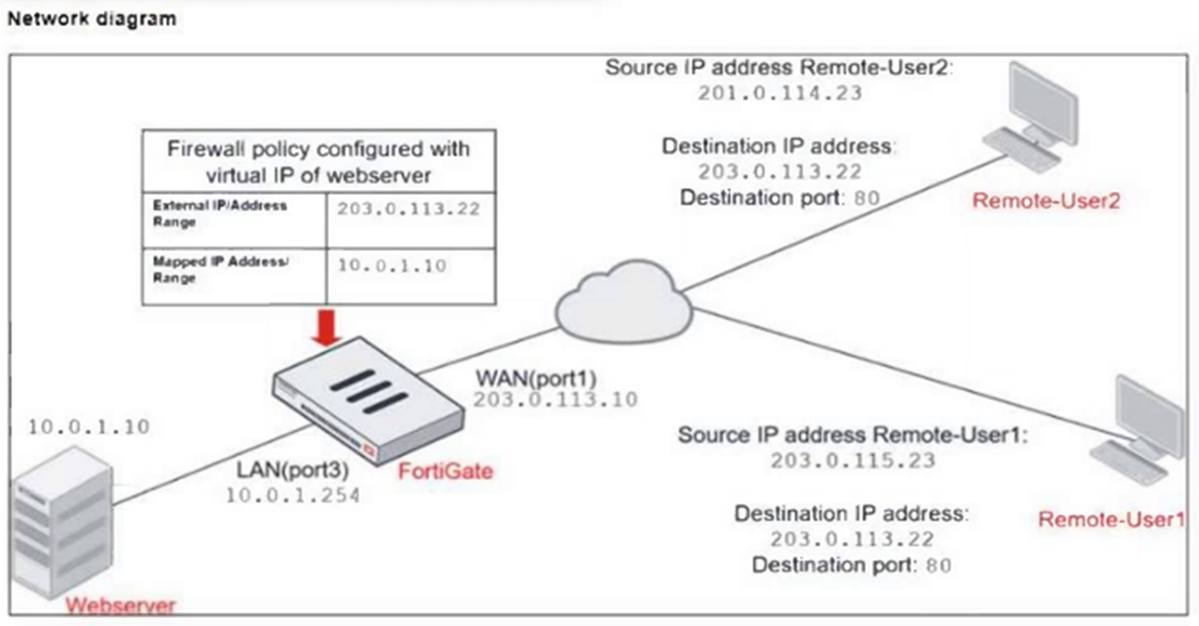
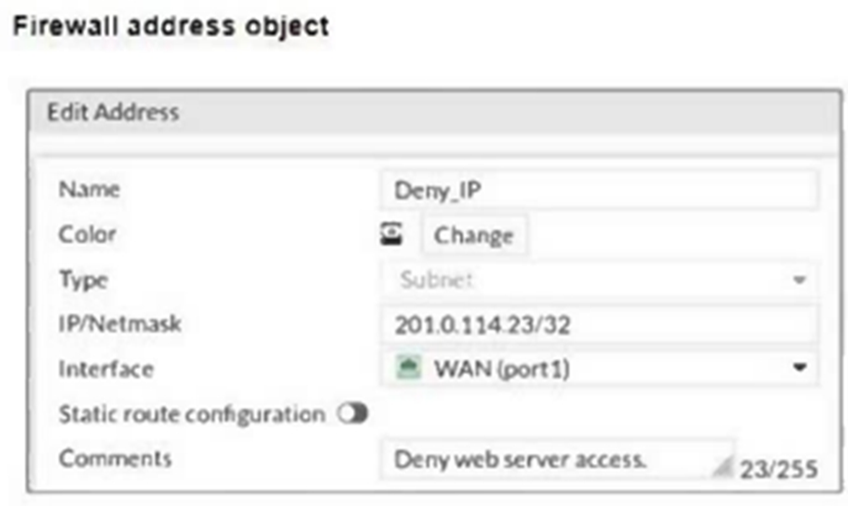
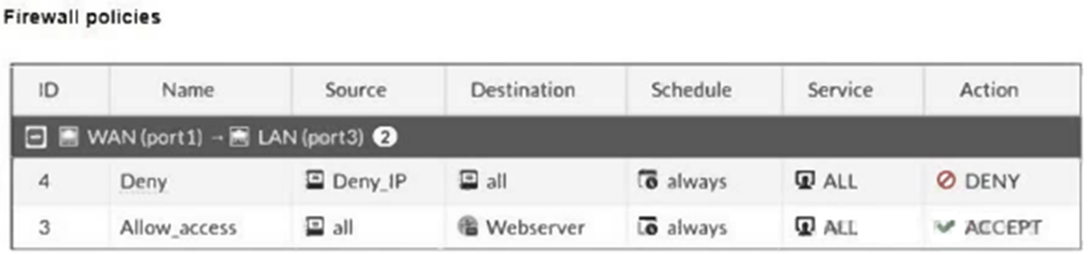
The exhibits show a diagram of a FortiGate device connected to the network, and the firewall configuration.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-User2.
The policy should work such that Remote-User1 must be able to access the Webserver while preventing Remote-User2 from accessing the Webserver.
Which two configuration changes can the administrator make to the policy to deny Webserver access for Remote-User2? (Choose two.)
Correct Answer:AB
Examine the IPS sensor and DoS policy configuration shown in the exhibit, then answer the question below.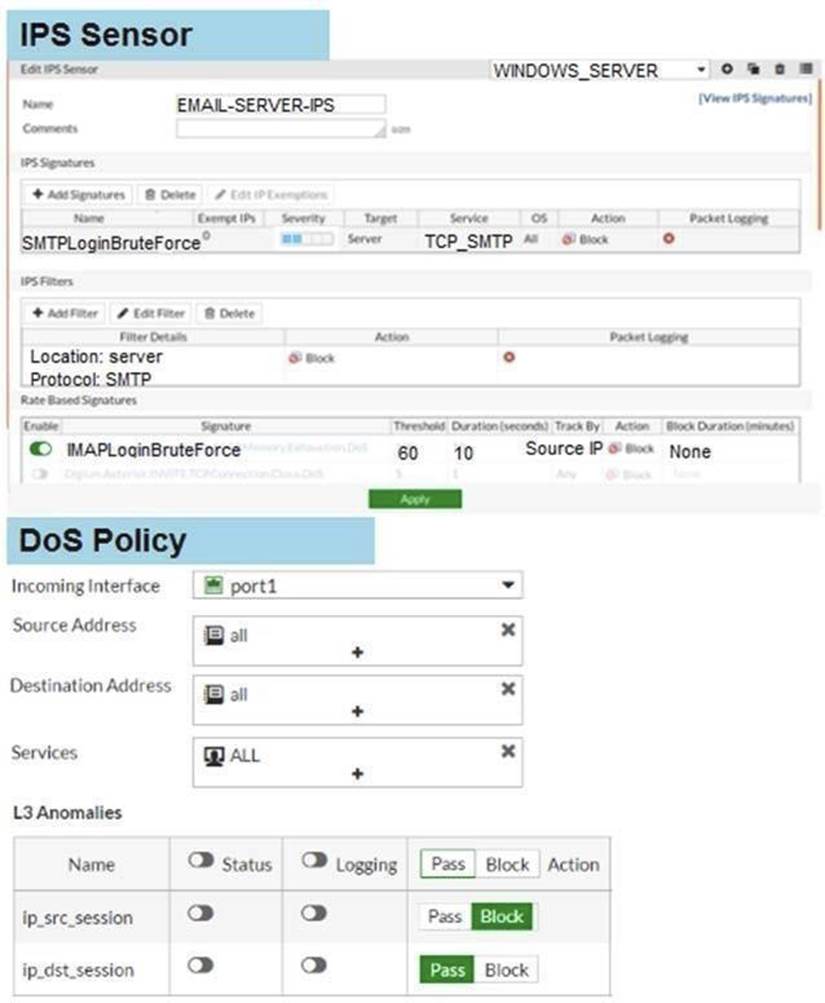
When detecting attacks, which anomaly, signature, or filter will FortiGate evaluate first?
Correct Answer:B
When FortiGate evaluates potential attacks, the IPS sensor follows a specific processing order based on the configuration of filters, signatures, and anomaly thresholds. In this case:
• The IPS sensor is configured with IMAP.Login.brute.Force, which comes first in the order of evaluation.
• FortiGate prioritizes based on signature definitions in the sensor, and since IMAP.Login.brute.Force appears higher in the configuration, it will be evaluated before the other signatures and anomalies.
Why the other options are less appropriate:
• A. SMTP.Login.Brute.Force: This would be evaluated after IMAP.Login.brute.Force, based on the sensor configuration hierarchy.
• C. ip_src_session: This is part of the DoS policy and does not come into play until after IPS signatures are evaluated.
• D. Location: server Protocol: SMTP: This appears to be part of the broader IPS sensor rule, but it is not the first item in the evaluation chain.
Which two settings are required for SSL VPN to function between two FortiGate devices? (Choose two.)
Correct Answer:BC
For SSL VPN to function correctly between two FortiGate devices, the following settings are required: B. The server FortiGate requires a CA certificate to verify the client FortiGate certificate: The server FortiGate must have a Certificate Authority (CA) certificate installed to authenticate and verify the certificate presented by the client FortiGate device.
B. The server FortiGate requires a CA certificate to verify the client FortiGate certificate: The server FortiGate must have a Certificate Authority (CA) certificate installed to authenticate and verify the certificate presented by the client FortiGate device. C. The client FortiGate requires a client certificate signed by the CA on the server FortiGate: The client FortiGate must have a client certificate that is signed by the same CA that the server FortiGate uses for verification. This ensures a secure SSL VPN connection between the two devices.
C. The client FortiGate requires a client certificate signed by the CA on the server FortiGate: The client FortiGate must have a client certificate that is signed by the same CA that the server FortiGate uses for verification. This ensures a secure SSL VPN connection between the two devices.
The other options are not directly necessary for establishing SSL VPN: A. The client FortiGate requires the SSL VPN tunnel interface type to connect SSL VPN: This is incorrect as SSL VPN does not require a specific tunnel interface type; it typically uses an SSL VPN client profile.
A. The client FortiGate requires the SSL VPN tunnel interface type to connect SSL VPN: This is incorrect as SSL VPN does not require a specific tunnel interface type; it typically uses an SSL VPN client profile. D. The client FortiGate requires a manually added route to remote subnets: While routing may be necessary, it is not specifically required for the SSL VPN functionality between two FortiGates.
D. The client FortiGate requires a manually added route to remote subnets: While routing may be necessary, it is not specifically required for the SSL VPN functionality between two FortiGates.
References FortiOS 7.4.1 Administration Guide - Configuring SSL VPN, page 1203.
FortiOS 7.4.1 Administration Guide - Configuring SSL VPN, page 1203.  FortiOS 7.4.1 Administration Guide - SSL VPN Authentication, page 1210.
FortiOS 7.4.1 Administration Guide - SSL VPN Authentication, page 1210.
Refer to the exhibit.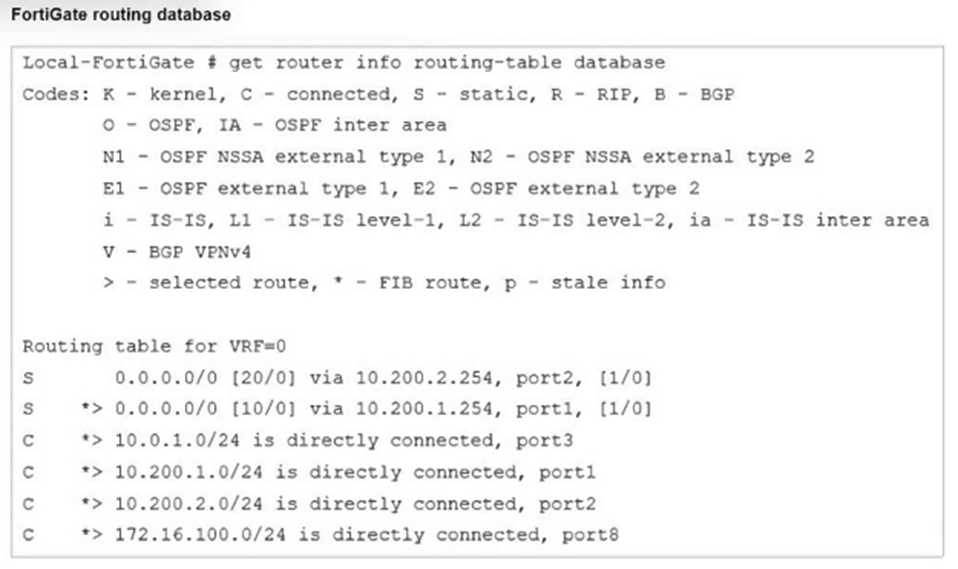
Which two statements are true about the routing entries in this database table? (Choose two.)
Correct Answer:CD
The routing table in the exhibit shows two default routes (0.0.0.0/0) with different administrative distances:  The default route through port2 has an administrative distance of 20.
The default route through port2 has an administrative distance of 20. The default route through port1 has an administrative distance of 10.
The default route through port1 has an administrative distance of 10.
Administrative distance determines the priority of the route; a lower value is preferred. Here, the route through port1 with an administrative distance of 10 is the preferred route. The route through port2 with an administrative distance of 20 acts as a standby or backup route. If the primary route (port1) fails or is unavailable, traffic will then be routed through port2.
Regarding the statement that the port2 interface is marked as inactive, there is no indication in the routing table that port2 is inactive. Similarly, all the routes displayed are not necessarily installed in the FortiGate routing table, as the table could include both active and backup routes.
References: FortiOS 7.4.1 Administration Guide: Default route configuration
FortiOS 7.4.1 Administration Guide: Default route configuration  FortiOS 7.4.1 Administration Guide: Routing table
FortiOS 7.4.1 Administration Guide: Routing table
Refer to the exhibit, which shows a partial configuration from the remote authentication server.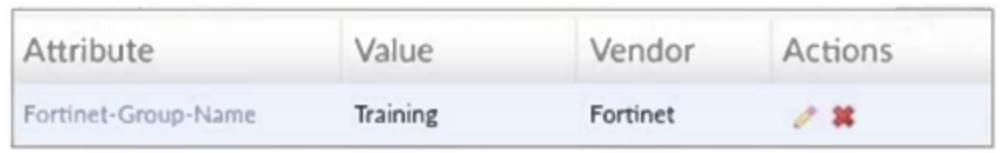
Why does the FortiGate administrator need this configuration?
Correct Answer:A