No Installation Required, Instantly Prepare for the FCSS_SASE_AD-23 exam and please click the below link to start the FCSS_SASE_AD-23 Exam Simulator with a real FCSS_SASE_AD-23 practice exam questions.
Use directly our on-line FCSS_SASE_AD-23 exam dumps materials and try our Testing Engine to pass the FCSS_SASE_AD-23 which is always updated.
Which secure internet access (SIA) use case minimizes individual workstation or device setup, because you do not needto install FortiClient on endpoints or configure explicit web proxy settings on web browser-based end points?
Correct Answer:B
The Secure Internet Access (SIA) use case that minimizes individual workstation or device setup is SIA for agentless remote users. This use case does not require installing FortiClient on endpoints or configuring explicit web proxy settings on web browser-based endpoints, making it the simplest and most efficient deployment.
✑ SIA for Agentless Remote Users:
✑ Minimized Setup:
References:
✑ FortiOS 7.2 Administration Guide: Details on different SIA deployment use cases and configurations.
✑ FortiSASE 23.2 Documentation: Explains how SIA for agentless remote users is implemented and the benefits it provides.
When you configure FortiSASE Secure Private Access (SPA) with SD-WAN integration, you must establish a routing adjacency between FortiSASE and the FortiGate SD-WAN hub. Which routing protocol must you use?
Correct Answer:A
When configuring FortiSASE Secure Private Access (SPA) with SD-WAN integration, establishing a routing adjacency between FortiSASE and the FortiGate SD- WAN hub requires the use of the Border Gateway Protocol (BGP).
✑ BGP (Border Gateway Protocol):
✑ Routing Adjacency:
References:
✑ FortiOS 7.2 Administration Guide: Provides information on configuring BGP for SD-WAN integration.
✑ FortiSASE 23.2 Documentation: Details on setting up routing adjacencies using BGP for Secure Private Access with SD-WAN.
Refer to the exhibits.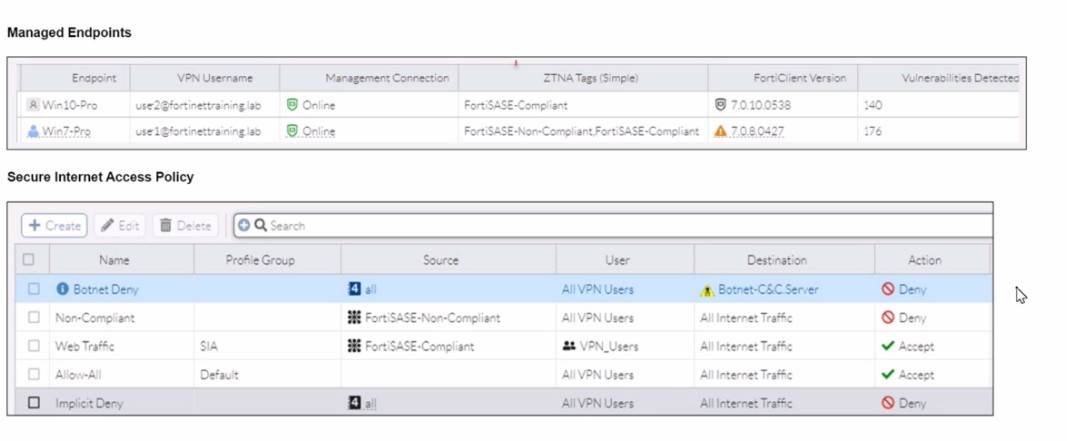
WiMO-Pro and Win7-Pro are endpoints from the same remote location. WiMO-Pro can
access the internet though FortiSASE, while Wm7-Pro can no longer access the internet Given the exhibits, which reason explains the outage on Wm7-Pro?
Correct Answer:D
Based on the provided exhibits, the reason why the Win7-Pro endpoint can no longer access the internet through FortiSASE is due to exceeding the total vulnerability detected threshold. This threshold is used to determine if a device is compliant with the security requirements to access the network.
✑ Endpoint Compliance:
✑ Vulnerability Threshold:
✑ Impact on Network Access:
References:
✑ FortiOS 7.2 Administration Guide: Provides information on endpoint compliance and vulnerability management.
✑ FortiSASE 23.2 Documentation: Explains how vulnerability thresholds are used to determine endpoint compliance and access control.
A FortiSASE administrator is configuring a Secure Private Access (SPA) solution to share endpoint information with a corporate FortiGate.
Which three configuration actions will achieve this solution? (Choose three.)
Correct Answer:ABC
To configure a Secure Private Access (SPA) solution to share endpoint information between FortiSASE and a corporate FortiGate, you need to take the following steps:
✑ Add the FortiGate IP address in the secure private access configuration on
FortiSASE:
✑ Use the FortiClient EMS cloud connector on the corporate FortiGate to connect to FortiSASE:
✑ Register FortiGate and FortiSASE under the same FortiCloud account:
References:
✑ FortiOS 7.2 Administration Guide: Provides details on configuring Secure Private Access and integrating with FortiGate.
✑ FortiSASE 23.2 Documentation: Explains how to set up and manage connections between FortiSASE and corporate FortiGate.
What are two advantages of using zero-trust tags? (Choose two.)
Correct Answer:AB
Zero-trust tags are critical in implementing zero-trust network access (ZTNA) policies. Here are the two key advantages of using zero-trust tags:
✑ Access Control (Allow or Deny):
✑ Determining Security Posture:
References:
✑ FortiOS 7.2 Administration Guide: Provides detailed information on configuring and using zero-trust tags for access control and security posture assessment.
✑ FortiSASE 23.2 Documentation: Explains how zero-trust tags are implemented and used within the FortiSASE environment for enhancing security and compliance.