No Installation Required, Instantly Prepare for the FCSS_SOC_AN-7.4 exam and please click the below link to start the FCSS_SOC_AN-7.4 Exam Simulator with a real FCSS_SOC_AN-7.4 practice exam questions.
Use directly our on-line FCSS_SOC_AN-7.4 exam dumps materials and try our Testing Engine to pass the FCSS_SOC_AN-7.4 which is always updated.
Which two statements about the FortiAnalyzer Fabric topology are true? (Choose two.)
Correct Answer:BD
The FortiAnalyzer Fabric topology is designed to centralize logging and analysis across multiple devices in a network.
It involves a hierarchy where the supervisor node manages and coordinates with other Fabric members.
Analyzing the Options:
Option A:Downstream collectors forwarding logs to Fabric members is not a typical configuration. Instead, logs are usually centralized to the supervisor.
Option B:For effective management and log centralization, logging devices must be registered to the supervisor. This ensures proper log collection and coordination.
Option C:The supervisor does not primarily use an API to store logs, incidents, and events locally. Logs are stored directly in the FortiAnalyzer database.
Option D:For the Fabric topology to function correctly, all Fabric members need to be in analyzer mode. This mode allows them to collect, analyze, and forward logs appropriately within the topology.
Conclusion:
The correct statements regarding the FortiAnalyzer Fabric topology are that logging devices must be registered to the supervisor and that Fabric members must be in analyzer mode.
References:
Fortinet Documentation on FortiAnalyzer Fabric Topology.
Best Practices for Configuring FortiAnalyzer in a Fabric Environment.
Which two playbook triggers enable the use of trigger events in later tasks as trigger variables? (Choose two.)
Correct Answer:AB
Understanding Playbook Triggers:
Playbook triggers are the starting points for automated workflows within FortiAnalyzer or FortiSOAR.
These triggers determine how and when a playbook is executed and can pass relevant information (trigger variables) to subsequent tasks within the playbook.
Types of Playbook Triggers:
EVENT Trigger:
Initiates the playbook when a specific event occurs.
The event details can be used as variables in later tasks to customize the response.
Selected as it allows using event details as trigger variables.
INCIDENT Trigger:
Activates the playbook when an incident is created or updated.
The incident details are available as variables in subsequent tasks.
Selected as it enables the use of incident details as trigger variables.
ON SCHEDULE Trigger:
Executes the playbook at specified times or intervals.
Does not inherently use trigger events to pass variables to later tasks.
Not selected as it does not involve passing trigger event details.
ON DEMAND Trigger:
Runs the playbook manually or as required.
Does not automatically include trigger event details for use in later tasks.
Not selected as it does not use trigger events for variables.
Implementation Steps:
Step 1: Define the conditions for the EVENT or INCIDENT trigger in the playbook configuration.
Step 2: Use the details from the trigger event or incident in subsequent tasks to customize actions and responses.
Step 3: Test the playbook to ensure that the trigger variables are correctly passed and utilized.
Conclusion:
EVENT and INCIDENT triggers are specifically designed to initiate playbooks based on specific occurrences, allowing the use of trigger details in subsequent tasks.
References:
Fortinet Documentation on Playbook Configuration FortiSOAR Playbook Guide
By using the EVENT and INCIDENT triggers, you can leverage trigger events in later tasks as variables, enabling more dynamic and responsive playbook actions.
Refer to the Exhibit: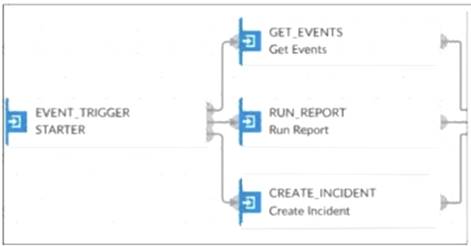
An analyst wants to create an incident and generate a report whenever FortiAnalyzer generates a malicious attachment event based on FortiSandbox analysis. The endpoint hosts are protected by FortiClient EMS integrated with FortiSandbox. All devices are logging to FortiAnalyzer.
Which connector must the analyst use in this playbook?
Correct Answer:A
Understanding the Requirements:
The objective is to create an incident and generate a report based on malicious attachment events detected by FortiAnalyzer from FortiSandbox analysis.
The endpoint hosts are protected by FortiClient EMS, which is integrated with FortiSandbox. All logs are sent to FortiAnalyzer.
Key Components:
FortiAnalyzer: Centralized logging and analysis for Fortinet devices.
FortiSandbox: Advanced threat protection system that analyzes suspicious files and URLs.
FortiClient EMS: Endpoint management system that integrates with FortiSandbox for endpoint protection.
Playbook Analysis:
The playbook in the exhibit consists of three main actions:GET_EVENTS,RUN_REPORT, andCREATE_INCIDENT.
EVENT_TRIGGER: Starts the playbook when an event occurs.
GET_EVENTS: Fetches relevant events.
RUN_REPORT: Generates a report based on the events.
CREATE_INCIDENT: Creates an incident in the incident management system.
Selecting the Correct Connector:
The correct connector should allow fetching events related to malicious attachments analyzed by FortiSandbox and facilitate integration with FortiAnalyzer.
Connector Options:
FortiSandbox Connector:
Directly integrates with FortiSandbox to fetch analysis results and events related to malicious attachments.
Best suited for getting detailed sandbox analysis results.
Selected as it is directly related to the requirement of handling FortiSandbox analysis events.
FortiClient EMS Connector:
Used for managing endpoint security and integrating with endpoint logs.
Not directly related to fetching sandbox analysis events.
Not selected as it is not directly related to the sandbox analysis events.
FortiMail Connector:
Used for email security and handling email-related logs and events.
Not applicable for sandbox analysis events.
Not selected as it does not relate to the sandbox analysis.
Local Connector:
Handles local events within FortiAnalyzer itself.
Might not be specific enough for fetching detailed sandbox analysis results.
Not selected as it may not provide the required integration with FortiSandbox.
Implementation Steps:
Step 1: Ensure FortiSandbox is configured to send analysis results to FortiAnalyzer.
Step 2: Use the FortiSandbox connector in the playbook to fetch events related to malicious attachments.
Step 3: Configure theGET_EVENTSaction to use the FortiSandbox connector.
Step 4: Set up theRUN_REPORTandCREATE_INCIDENTactions based on the fetched events.
References:
Fortinet Documentation on FortiSandbox Integration FortiSandbox Integration Guide
Fortinet Documentation on FortiAnalyzer Event Handling FortiAnalyzer Administration Guide
By using the FortiSandbox connector, the analyst can ensure that the playbook accurately fetches events based on FortiSandbox analysis and generates the required incident and report.
Refer to the exhibit.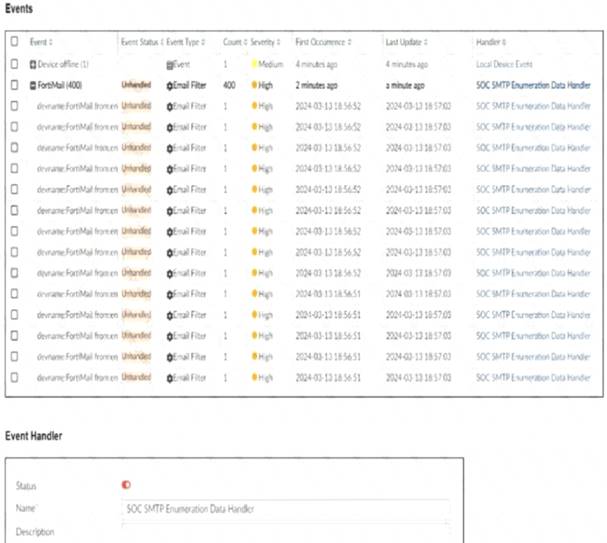
You notice that the custom event handler you configured to detect SMTP reconnaissance activities is creating a large number of events. This is overwhelming your notification system.
How can you fix this?
Correct Answer:A
Understanding the Issue:
The custom event handler for detecting SMTP reconnaissance activities is generating a large number of events.
This high volume of events is overwhelming the notification system, leading to potential alert fatigue and inefficiency in incident response.
Event Handler Configuration:
Event handlers are configured to trigger alerts based on specific criteria.
The frequency and volume of these alerts can be controlled by adjusting the trigger conditions.
Possible Solutions:
* A. Increase the trigger count so that it identifies and reduces the count triggered by a particular group:
By increasing the trigger count, you ensure that the event handler only generates alerts after a higher threshold of activity is detected.
This reduces the number of events generated and helps prevent overwhelming the notification system.
Selected as it effectively manages the volume of generated events.
* B. Disable the custom event handler because it is not working as expected:
Disabling the event handler is not a practical solution as it would completely stop monitoring for SMTP reconnaissance activities.
Not selected as it does not address the issue of fine-tuning the event generation.
* C. Decrease the time range that the custom event handler covers during the attack:
Reducing the time range might help in some cases, but it could also lead to missing important activities if the attack spans a longer period.
Not selected as it could lead to underreporting of significant events.
* D. Increase the log field value so that it looks for more unique field values when it creates the event:
Adjusting the log field value might refine the event criteria, but it does not directly control the volume of alerts.
Not selected as it is not the most effective way to manage event volume.
Implementation Steps:
Step 1: Access the event handler configuration in FortiAnalyzer.
Step 2: Locate the trigger count setting within the custom event handler for SMTP reconnaissance.
Step 3: Increase the trigger count to a higher value that balances alert sensitivity and volume.
Step 4: Save the configuration and monitor the event generation to ensure it aligns with expected levels.
Conclusion:
By increasing the trigger count, you can effectively reduce the number of events generated by the custom event handler, preventing the notification system from being overwhelmed.
References:
Fortinet Documentation on Event Handlers and Configuration FortiAnalyzer Administration Guide
Best Practices for Event Management Fortinet Knowledge Base
By increasing the trigger count in the custom event handler, you can manage the volume of generated events and prevent the notification system from being overwhelmed.
Which FortiAnalyzer connector can you use to run automation stitches9
Correct Answer:D
 Overview of Automation Stitches:
Overview of Automation Stitches: Automation stitches in FortiAnalyzer are predefined sets of automated actions triggered by specific events. These actions help in automating responses to security incidents, improving efficiency, and reducing the response time.
Automation stitches in FortiAnalyzer are predefined sets of automated actions triggered by specific events. These actions help in automating responses to security incidents, improving efficiency, and reducing the response time. FortiAnalyzer Connectors:
FortiAnalyzer Connectors: FortiAnalyzer integrates with various Fortinet products and other third-party solutions through connectors. These connectors facilitate communication and data exchange, enabling centralized management and automation.
FortiAnalyzer integrates with various Fortinet products and other third-party solutions through connectors. These connectors facilitate communication and data exchange, enabling centralized management and automation. Available Connectors for Automation Stitches:
Available Connectors for Automation Stitches:  FortiCASB:
FortiCASB: FortiCASB is a Cloud Access Security Broker that helps secure SaaS applications.
FortiCASB is a Cloud Access Security Broker that helps secure SaaS applications.
However, it is not typically used for running automation stitches within FortiAnalyzer.