Which of the following is true for XSS, SQL injection, and RFI?
Correct Answer:C
Which of the following techniques is used to identify attacks originating from a botnet?
Correct Answer:C
An attacker changes the address of a sub-routine in such a manner that it begins to point to the address of the malicious code. As a result, when the function has been exited, the application can be forced to shift to the malicious code. The image given below explains this phenomenon: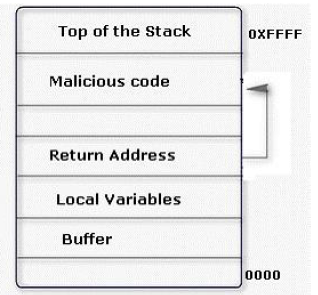
Which of the following tools can be used as a countermeasure to such an attack?
Correct Answer:B
Sandra, an expert computer user, hears five beeps while booting her computer that has AMI BIOS; and after that her computer stops responding. Sandra knows that during booting process POST produces different beep codes for different types of errors. Which of the following errors refers to this POST beep code?
Correct Answer:D
Which of the following types of firewall functions at the Session layer of OSI model?
Correct Answer:A