Which of the following protocols uses only User Datagram Protocol (UDP)?
Correct Answer:C
Which of the following tools is used to detect spam email without checking the content?
Correct Answer:C
Adam works as a professional Computer Hacking Forensic Investigator. He wants to investigate a suspicious email that is sent using a Microsoft Exchange server. Which of the following files will he review to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
Correct Answer:ABC
Which of the following types of write blocker device uses one interface for one side and a different one for the other?
Correct Answer:B
The following output is generated by running the show ip route command:
RouterA#show ip route
< - - Output Omitted for brevity - -> 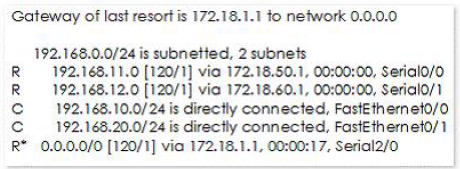
Which next hop address will RouterA use in forwarding traffic to 10.10.100.0/24?
Correct Answer:C