In which of the following attacks does an attacker spoof the source address in IP packets that are sent to the victim?
Correct Answer:C
John works as a Network Security Professional. He is assigned a project to test the security of www.we-are-secure.com. He establishes a connection to a target host running a Web service with netcat and sends a bad html request in order to retrieve information about the service on the host.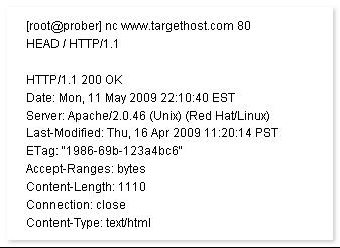
Which of the following attacks is John using?
Correct Answer:D
Which of the following tools is described in the statement given below?
"It has a database containing signatures to be able to detect hundreds of vulnerabilities in UNIX, Windows, and commonly used web CGI scripts. Moreover, the database detects DdoS zombies and Trojans as well."
Correct Answer:B
Which of the following rootkits is used to attack against full disk encryption systems?
Correct Answer:A
203 ms 22.670 ms 20.111 ms 13 0.so-2-0-0.TL1.NYC8.ALTER.NET (152.63.0.153) 30.929 ms 24.858 ms
Solution:
Does this meet the goal?
Correct Answer:A