- (Topic 1)
Which of the following is prepared by the business and serves as a starting point for producing the IT Service Continuity Strategy?
Correct Answer:B
- (Topic 2)
What are packet sniffers?
Correct Answer:D
- (Topic 2)
Maria works as a professional Ethical Hacker. She is assigned a project to test the security of www.we-are-secure.com. She wants to test a DoS attack on the We-are-secure server. She finds that the firewall of the server is blocking the ICMP messages, but it is not checking the UDP packets. Therefore, she sends a large amount of UDP echo request traffic to the IP broadcast addresses. These UDP requests have a spoofed source address of the We-are-secure server. Which of the following DoS attacks is Maria using to accomplish her task?
Correct Answer:C
- (Topic 2)
You work as a Consumer Support Technician for ABC Inc. The company provides troubleshooting support to users. You are troubleshooting a computer of a user who is working on Windows Vista.
He reports that his sensitive data is being accessed by someone because of security vulnerability in the component of Windows Vista. Which of the following features of Windows Security Center will you configure to save the user's data?
Correct Answer:C
- (Topic 2)
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases.
The email header of the suspicious email is given below: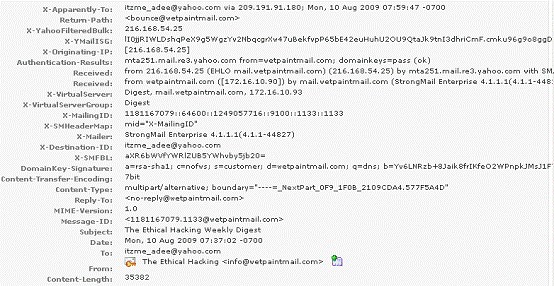
What is the IP address of the sender of this email?
Correct Answer:D