- (Topic 1)
Which type of Cross-Sire Scripting (XSS> vulnerability is hardest for automated testing tools to detect, and for what reason?
Correct Answer:A
- (Topic 4)
Which of the following types of Penetration testing provides the testers with complete knowledge of the infrastructure to be tested?
Correct Answer:A
- (Topic 2)
What happens when you scan a broadcast IP address of a network?
Each correct answer represents a complete solution. Choose all that apply.
Correct Answer:AB
- (Topic 1)
A penetration tester wishes to stop the Windows Firewall process on a remote host running Windows Vista She issues the following commands: 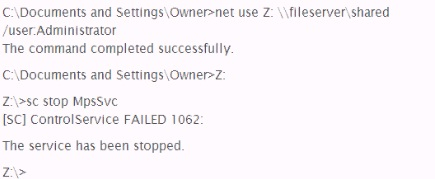
A check of the remote host indicates that Windows Firewall is still running. Why did the command fail?
Correct Answer:C
- (Topic 3)
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.we-are-secure.com. He enters a single quote in the input field of the login page of the Weare- secure Web site and receives the following error message:
Microsoft OLE DB Provider for ODBC Drivers error '0x80040E14'
This error message shows that the We-are-secure Website is vulnerable to __________.
Correct Answer:A