- (Topic 1)
When attempting to crack a password using Rainbow Tables, what is the output of the
reduction function?
Correct Answer:D
Reference:
http://en.wikipedia.org/wiki/Rainbow_table
- (Topic 1)
A customer has asked for a scan or vulnerable SSH servers. What is the penetration tester attempting to accomplish using the following Nmap command? 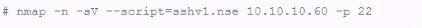
Correct Answer:D
- (Topic 2)
Which protocol would need to be available on a target in order for Nmap to identify services like IMAPS and POP3S?
Correct Answer:A
Reference:
http://nmap.org/book/vscan.html
- (Topic 3)
GSM uses either A5/1 or A5/2 stream cipher for ensuring over-the-air voice privacy. Which
of the following cryptographic attacks can be used to break both ciphers?
Correct Answer:B
- (Topic 4)
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He is using a tool to crack the wireless encryption keys. The description of the tool is as follows: 
Which of the following tools is John using to crack the wireless encryption keys?
Correct Answer:B