- (Topic 2)
Which of the following methods will free up bandwidth in a Wireless LAN (WLAN)?
Correct Answer:B
- (Topic 1)
Which of the following best describes a server side exploit?
Correct Answer:C
- (Topic 3)
Which of the following attacks allows an attacker to recover the key in an RC4 encrypted stream from a large number of messages in that stream?
Correct Answer:D
- (Topic 2)
Analyze the output of the two commands below: 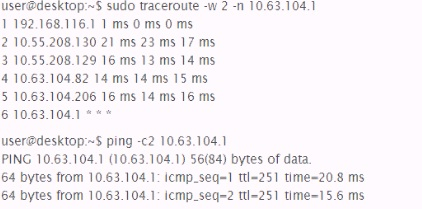
Which of the following can be factually inferred from the results of these commands?
Correct Answer:C
- (Topic 3)
The employees of EWS Inc. require remote access to the company's Web servers. In order to provide solid wireless security, the company uses EAP-TLS as the authentication protocol. Which of the following statements are true about EAP-TLS?
Each correct answer represents a complete solution. Choose all that apply.
Correct Answer:AB