168.116.9 Is an IP address forvvww.scanned-server.com. Why are the results from the two scans, shown below, different?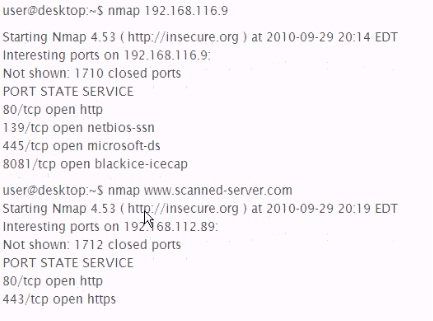
Correct Answer:C
- (Topic 2)
You want to create a binary log file using tcpdump. Which of the following commands will you use?
Correct Answer:C
- (Topic 1)
Which Metasploitvncinject stager will allow VNC communications from the attacker to a listening port of the attacker's choosing on the victim machine?
Correct Answer:B
Reference: http://www.rapid7.com/db/modules/payload/windows/vncinject/reverse_tcp
- (Topic 3)
TCP/IP stack fingerprinting is the passive collection of configuration attributes from a remote device during standard layer 4 network communications. The combination of parameters may then be used to infer the remote operating system (OS fingerprinting), or incorporated into a device fingerprint. Which of the following Nmap switches can be used to perform TCP/IP stack fingerprinting?
Correct Answer:A
- (Topic 4)
Which of the following is the most common method for an attacker to spoof email?
Correct Answer:D