- (Topic 1)
Analyze the screenshot below. What type of vulnerability is being attacked? 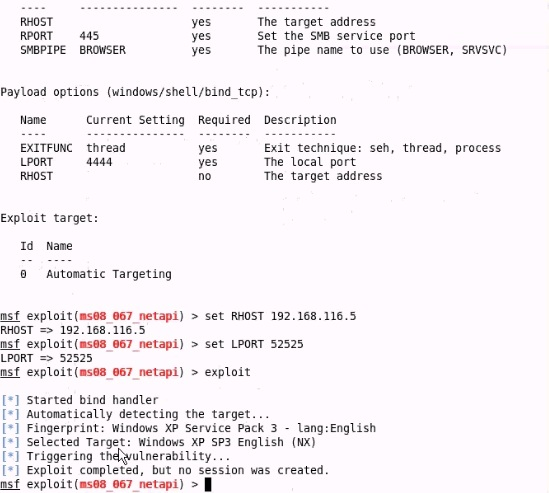
Correct Answer:B
- (Topic 3)
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He wants to perform a stealth scan to discover open ports and applications running on the We-are-secure server. For this purpose, he wants to initiate scanning with the IP address of any third party. Which of the following scanning techniques will John use to accomplish his task?
Correct Answer:C
- (Topic 2)
What will the following scapy commands do? 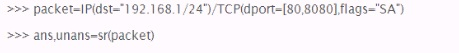
Correct Answer:D
- (Topic 2)
Which of the following tools allow you to perform HTTP tunneling?
Each correct answer represents a complete solution. Choose all that apply.
Correct Answer:ABD
- (Topic 4)
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He performs a Teardrop attack on the we-are-secure server and observes that the server crashes. Which of the following is the most likely cause of the server crash?
Correct Answer:B