In preparation to do a vulnerability scan against your company's systems. You've taken the steps below:
You've notified users that there will be a system test.
You've priontized and selected your targets and subnets.
You've configured the system to do a deep scan.
You have a member of your team on call to answer questions.
Which of the following is a necessary step to take prior to starting the scan?
Correct Answer:C
You are implementing wireless access at a defense contractor. Specifications say, you must implement the AES Encryption algorithm. Which encryption standard should you choose?
Correct Answer:D
IPS devices that are classified as "In-line NIDS" devices use a combination of anomaly analysis, signature-based rules, and what else to identify malicious events on the network?
Correct Answer:B
Included below is the output from a resource kit utility run against local host.
Which command could have produced this output? 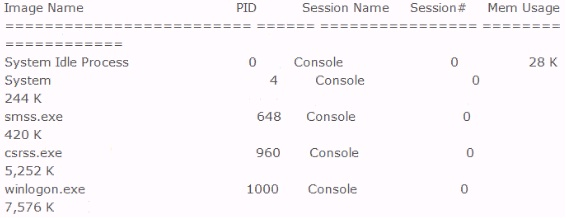
Correct Answer:D
Which of the following TCP dump output lines indicates the first step in the TCP 3-way handshake?
Correct Answer:A