- (Topic 2)
Which of the following applications work as mass-emailing worms? (Choose two)
Correct Answer:BC
The Nimda and I LOVE YOU viruses work as mass-emailing worms.
- (Topic 1)
eBox Platform is an open source unified network server (or a Unified Network Platform) for SMEs. In which of the following forms can eBox Platform be used?
Correct Answer:ABC
eBox Platform is an open source unified network server (or a Unified Network Platform) for SMEs. eBox Platform can act as a Gateway, Network Infrastructure Manager, Unified Threat Manager, Office Server, Unified Communications Server or a combination of them. Besides, eBox Platform includes a development framework to ease the development of new Unix-based services. Answer D is incorrect. eBox Platform cannot act as a sandbox. A sandbox is a security mechanism for separating running programs. It is often used to execute untested code, or untrusted programs, from unverified third-parties, suppliers, and untrusted users.
- (Topic 4)
Mark works as a Database Administrator for MarLinc Inc. How will he execute a SQL command from the SQL buffer?
Correct Answer:BE
SQL buffer stores the most recently used SQL commands and PL/SQL blocks. It does not store the SQL* Plus commands. The SQL buffer can be edited or saved to a file. A SQL command or a PL/SQL block can be executed by entering a semicolon (;) or a slash (/), or by using the RUN command at the command prompt. When a semicolon (;) is entered at the end of a command, the command is completed and executed. When a slash (/) is entered on a new line, the command in the buffer is executed. It can also be used to execute a PL/SQL block. The RUN command is used to execute a command in the buffer. A SQL command can be saved in the buffer by entering a blank line. Reference: Oracle8i Online Documentation, Contents: "SQL*PLUS Users Guide and Reference", "Learning SQL*PLUS Basics, 3 of 4"
- (Topic 4)
You work as a Network Administrator for XYZ CORP. The company has a TCP/IP-based network environment. The network contains Cisco switches and a Cisco router. A user is unable to access the Internet from Host B. You also verify that Host B is not able to connect to other resources on the network. The IP configuration of Host B is shown below: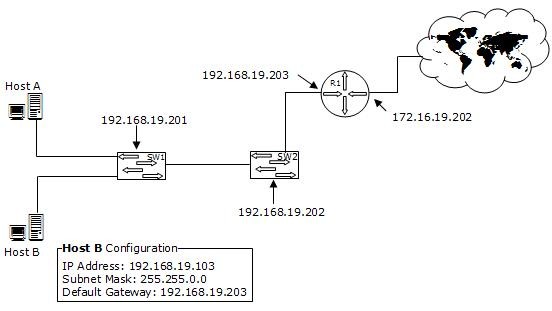
Which of the following is the most likely cause of the issue?
Correct Answer:A
According to the network diagram, the IP address range used on the network is from the class C private address range. The class C IP address uses the following default subnet mask: 255.255.255.0 The question specifies that the subnet mask used in Host B is 255.255.0.0, which is an incorrect subnet mask.
- (Topic 1)
John works as a contract Ethical Hacker. He has recently got a project to do security checking for www.we-are-secure.com. He wants to find out the operating system of the we- are-secure server in the information gathering step. Which of the following commands will he use to accomplish the task? (Choose two)
Correct Answer:BD
According to the scenario, John will use "nmap -v -O 208.100.2.25" to detect the operating system of the we-are-secure server. Here, -v is used for verbose and -O is used for TCP/IP fingerprinting to guess the remote operating system. John may also use the DNS name of we-are-secure instead of using the IP address of the we-are-secure server. So, he can also use the nmap command "nmap -v -O www.we-are-secure.com ". Answer C is incorrect. "nc -v -n 208.100.2.25 80" is a Netcat command, which is used to banner grab for getting information about the