- (Exam Topic 4)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
A user named User1 has a computer named Computer1 that runs Windows 10. Computer1 is joined to an Azure Active Directory (Azure AD) tenant named contoso.com. User1 joins Computer1 to contoso.com by using user1@contoso.com.
Computer1 contains a folder named Folder1. Folder1 is in drive C and is shared as Share1. Share1 has the permission shown in the following table.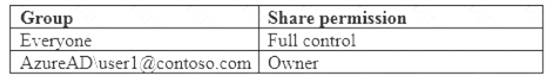
A user named User2 has a computer named Computer2 that runs Windows 10. User2 joins Computer2 to contoso.com by using user2@contoso.com.
User2 attempts to access Share1 and receives the following error message: “The username or password is incorrect.”
You need to ensure that User2 can connect to Share1.
Solution: In Azure AD, you create a group named Group1 that contains User1 and User2. You grant Group1 Modify access to Folder1.
Does this meet the goal?
Correct Answer:A
References:
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc75417
- (Exam Topic 4)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com. The domain contains the users shown in the following table.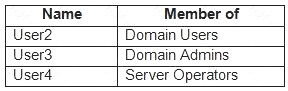
You have a computer named Computer1 that runs Windows 10 and is in a workgroup.
A local standard user on Computer1 named User1 joins the computer to the domain and uses the credentials of User2 when prompted.
You need to ensure that you can rename Computer1 as Computer33. Solution: You use the credentials of User4 on Computer1.
Does this meet the goal?
Correct Answer:B
Renaming a domain-joined computer will also rename the computer account in the domain. To do this, you need domain administrator privileges.
User4 is a server operator, not an administrator. Members of the Server Operators group can sign in to a server interactively, create and delete network shared resources, start and stop services, back up and restore files, format the hard disk drive of the computer, and shut down the computer.
Use User3's credentials instead.
References:
https://docs.microsoft.com/en-us/windows/security/identity-protection/access-control/active-directory-security-g
- (Exam Topic 2)
You need to meet the technical requirement for User6. What should you do?
Correct Answer:B
- (Exam Topic 4)
You have a computer that runs Windows 10 and has File History enabled. File History is configured to save copies of files every 15 minutes.
At 07:55, you create a file named D:Folder1File1.docx.
You add D:Folder1 to File History and manually run File History at 08:00. You modify File1.docx at the following times: 08:05
08:05 08:12
08:12 08:20
08:20 08:24
08:24 08:50
08:50
At 08:55, you attempt to restore File1.docx.
How many previous versions of File1.docx will be available to restore?
Correct Answer:C
- (Exam Topic 4)
Your network contains an Active Directory domain. The domain contains three computers named Computer1, Computer2, and Computer3 that run Windows 10. The computers are on the same network and have network connectivity.
Windows Defender Firewall on Computer1 has the server-to-server connection security rule shown in the following table.
Windows Defender Firewall on Computer2 has the server-to-server connection security rule shown in the following table.
Windows Defender Firewall on Computer3 has the server-to-server connection security rule shown in the following table.
All the connection security rules are enabled and configured to use only the Computer (Kerberos VS) authentication method.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.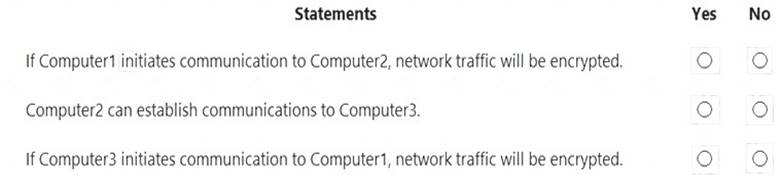
Solution:
Graphical user interface, text, application Description automatically generated
References:
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-firewall/create-an-authentication
Does this meet the goal?
Correct Answer:A