- (Exam Topic 5)
You have a Microsoft 365 E5 subscription.
You plan to implement Microsoft 365 compliance policies to meet the following requirements: Identify documents that are stored in Microsoft Teams and SharePoint Online that contain Personally Identifiable Information (PII).
Identify documents that are stored in Microsoft Teams and SharePoint Online that contain Personally Identifiable Information (PII). Report on shared documents that contain PII. What should you create?
Report on shared documents that contain PII. What should you create?
Correct Answer:B
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-learn-about-dlp?view=o365-worldwide
- (Exam Topic 5)
You have a Microsoft 365 E5 subscription that uses Microsoft Intune. You have devices enrolled in Intune as shown in the following table.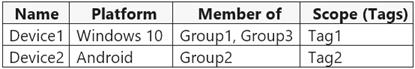
You create the device configuration profiles shown in the following table.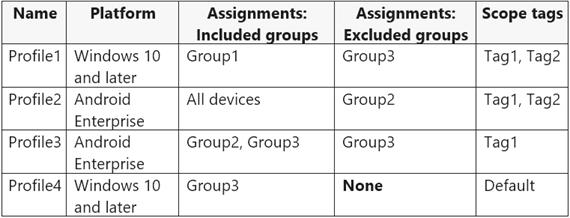
Which profiles will be applied to each device? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.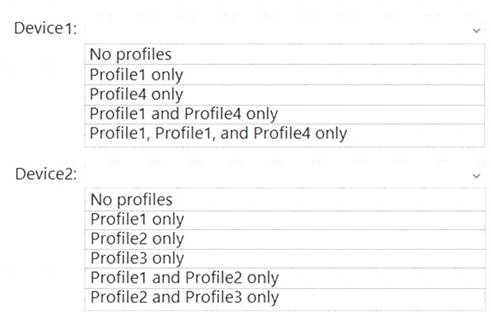
Solution:
Graphical user interface, text, application, table Description automatically generated
Does this meet the goal?
Correct Answer:A
- (Exam Topic 5)
You have a Microsoft 365 E5 subscription.
Users access Microsoft 365 from both their laptop and a corporate Virtual Desktop Infrastructure (VDI) solution.
From Azure AD Identity Protection, you enable a sign-in risk policy.
Users report that when they use the VDI solution, they are regularly blocked when they attempt to access Microsoft 365.
What should you configure?
Correct Answer:B
There are two types of risk policies in Azure Active Directory (Azure AD) Conditional Access you can set up to automate the response to risks and allow users to self-remediate when risk is detected:
Sign-in risk policy User risk policy
Configured trusted network locations are used by Identity Protection in some risk detections to reduce false positives.
Reference:
https://learn.microsoft.com/en-us/azure/active-directory/identity-protection/howto-identity-protection-configure- https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/location-condition
- (Exam Topic 5)
DRAG DROP
Your network contains an on-premises Active Directory domain that syncs to Azure Active Directory (Azure AD). The domain contains the servers shown in the following table.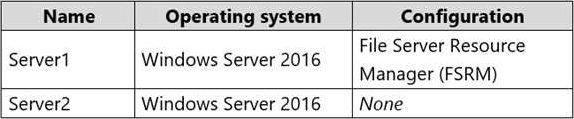
You use Azure Information Protection.
You need to ensure that you can apply Azure Information Protection labels to the file stores on Server1. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.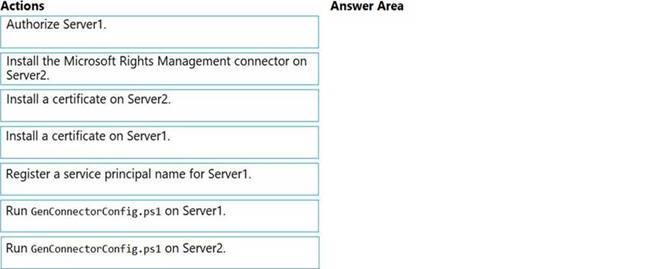
Solution:
Reference:
https://docs.microsoft.com/en-us/azure/information-protection/install-configure-rms-connector https://docs.microsoft.com/en-us/azure/information-protection/configure-servers-rms-connector
Does this meet the goal?
Correct Answer:A
- (Exam Topic 5)
You have a Microsoft 365 subscription that uses Microsoft Defender for Office 365. A Built-in protection preset security policy is applied to the subscription.
Which two policy types will be applied by the Built-in protection policy? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Correct Answer:CE