- (Exam Topic 2)
You need to meet the technical requirement for the SharePoint administrator. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.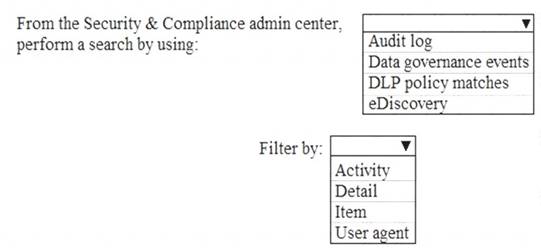
Solution:
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/search-the-audit-log-in-security-and-compliance
Does this meet the goal?
Correct Answer:A
- (Exam Topic 5)
HOTSPOT
You have a Microsoft 365 E5 subscription. You need to meet the following requirements:
Automatically encrypt documents stored in Microsoft OneDrive and SharePoint.
Enable co-authoring for Microsoft Office documents encrypted by using a sensitivity label.
Which two settings should you use in the Microsoft Purview compliance portal? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.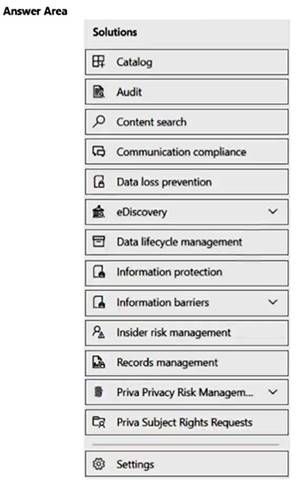
Solution:
Box 1: Information protection
Automatically encrypt documents stored in Microsoft OneDrive and SharePoint.
How to integrate Microsoft Purview Information Protection with Defender for Cloud Apps Enable Microsoft Purview Information Protection
All you have to do to integrate Microsoft Purview Information Protection with Defender for Cloud Apps is
select a single checkbox. By enabling automatic scan, you enable searching for sensitivity labels from Microsoft Purview Information Protection on your Office 365 files without the need to create a policy. After you enable it, if you have files in your cloud environment that are labeled with sensitivity labels from Microsoft Purview Information Protection, you'll see them in Defender for Cloud Apps.
To enable Defender for Cloud Apps to scan files with content inspection enabled for sensitivity labels: In the Microsoft 365 Defender portal, select Settings. Then choose Cloud Apps. Then go to Information
Protection -> Microsoft Information Protection.
Note: Encryption of data at rest
Encryption at rest includes two components: BitLocker disk-level encryption and per-file encryption of customer content.
BitLocker is deployed for OneDrive for Business and SharePoint Online across the service. Per-file encryption is also in OneDrive for Business and SharePoint Online in Microsoft 365 multi-tenant and new dedicated environments that are built on multi-tenant technology.
Box 2: Settings
Enable co-authoring for Microsoft Office documents encrypted by using a sensitivity label.
* 1. Sign in to the Microsoft Purview compliance portal as a global admin for your tenant.
* 2. From the navigation pane, select Settings > Co-authoring for files with sensitivity files.
* 3. On the Co-authoring for files with sensitivity labels page, read the summary description, prerequisites, and what to expect.
* 4. Then select Turn on co-authoring for files with sensitivity labels, and Apply.
* 5. Wait 24 hours for this setting to replicate across your environment before you use this new feature for co-authoring.
Reference:
https://learn.microsoft.com/en-us/defender-cloud-apps/azip-integration https://learn.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels-coauthoring
Does this meet the goal?
Correct Answer:A
- (Exam Topic 2)
You need to meet the technical requirement for large-volume document retrieval. What should you create?
Correct Answer:D
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/activity-policies-and-alerts
- (Exam Topic 5)
HOTSPOT
Your network contains an on-premises Active Directory domain and a Microsoft 365 subscription. The domain contains the users shown in the following table.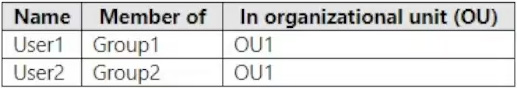
The domain contains the groups shown in the following table.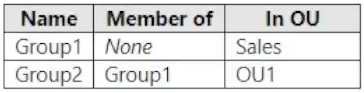
You are deploying Azure AD Connect.
You configure Domain and OU filtering as shown in the following exhibit.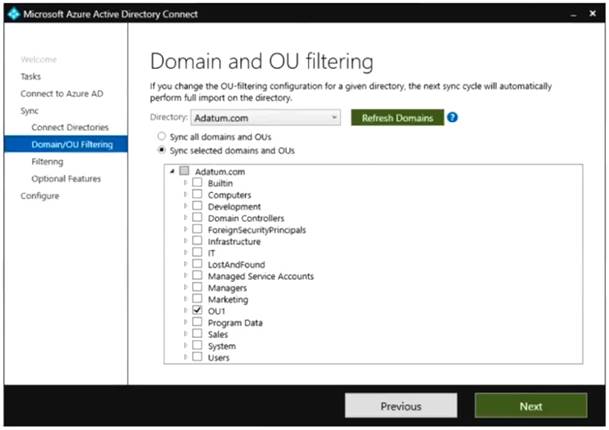
You configure Filter users and devices as shown in the following exhibit.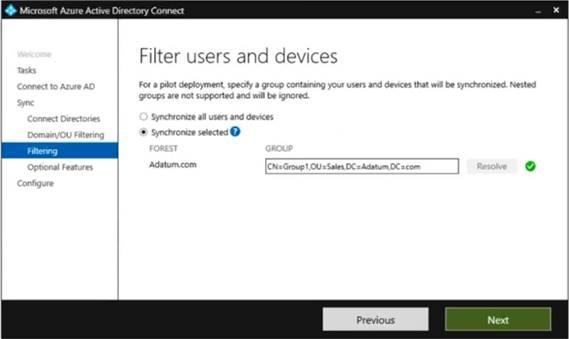
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.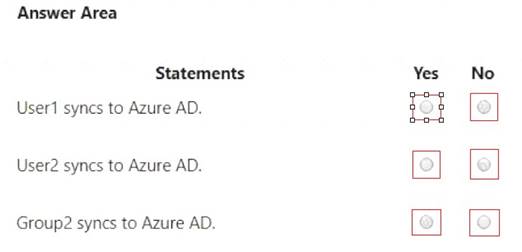
Solution: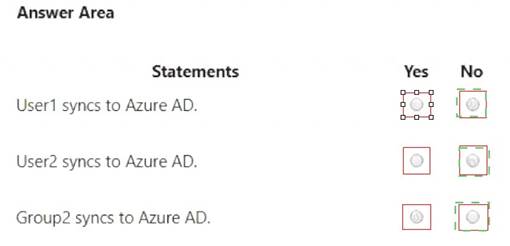
Does this meet the goal?
Correct Answer:A
- (Exam Topic 5)
You have a Microsoft 365 subscription that contains a user named User1.
You need to ensure that User1 can search the Microsoft 365 audit logs from the Security & Compliance admin center.
Which role should you assign to User1?
Correct Answer:B
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/search-the-audit-log-in-security-and-compliance?vi