- (Exam Topic 5)
You have a Microsoft 365 subscription that uses Microsoft Defender for Office 365. You need to configure policies to meet the following requirements: Customize the common attachments filter.
Customize the common attachments filter. Enable impersonation protection for sender domains.
Enable impersonation protection for sender domains.
Which type of policy should you configure for each requirement? To answer, drag the appropriate policy types to the correct requirements. Each policy type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Solution:
A close-up of a question Description automatically generated
Box 1: Anti-malware
Customize the common attachments filter. See step 5 below.
* 1. Use the Microsoft 365 Defender portal to create anti-malware policies
In the Microsoft 365 Defender portal at https://security.microsoft.com, go to Email & Collaboration > Policies
& Rules > Threat policies > Anti-Malware in the Policies section. To go directly to the Anti-malware page, use https://security.microsoft.com/antimalwarev2
* 2. On the Anti-malware page, select Create to open the new anti-malware policy wizard. On the Name your policy page, configure these settings:
Name: Enter a unique, descriptive name for the policy. Description: Enter an optional description for the policy.
* 3. When you're finished on the Name your policy page, select Next.
* 4. On the Users and domains page, identify the internal recipients that the policy applies to (recipient conditions)
* 5. On the Protection settings page, configure the following settings: Protection settings section:
Enable the common attachments filter: If you select this option, messages with the specified attachments are treated as malware and are automatically quarantined. You can modify the list by clicking Customize file types and selecting or deselecting values in the list.
* 6. Etc.
Box 2: Anti-phishing
Enable impersonation protection for sender domains. Anti-phishing policies in Microsoft 365
The high-level differences between anti-phishing policies in EOP and anti-phishing policies in Defender for Office 365 are described in the following table:
Reference:
https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/anti-malware-policies-configure https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/anti-phishing-policies-about
Does this meet the goal?
Correct Answer:A
- (Exam Topic 5) You have a Microsoft 365 E5 tenant. You configure sensitivity labels.
Users report that the Sensitivity button is unavailability in Microsoft Word for the web. The sensitivity button is available in Word for Microsoft 365.
You need to ensure that the users can apply the sensitivity labels when they use Word for the web. What should you do?
Correct Answer:B
- (Exam Topic 5)
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint.
When users attempt to access the portal of a partner company, they receive the message shown in the following exhibit.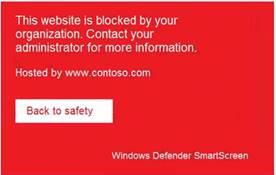
You need to enable user access to the partner company's portal. Which Microsoft Defender for Endpoint setting should you modify?
Correct Answer:E
This Website Is Blocked By Your Organization
Custom indicators will block malicious IPs, URLs, and domains. Then, they will display the above message for the user.
Reference:
https://jadexstrategic.com/web-protection/
- (Exam Topic 5)
You have a Microsoft 365 E5 subscription.
You plan to implement records management and enable users to designate documents as regulatory records. You need to ensure that the option to mark content as a regulatory record is visible when you create retention labels.
What should you do first?
Correct Answer:C
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/declare-records?view=o365-worldwide
- (Exam Topic 5)
HOTSPOT
You have a Microsoft 365 E5 subscription that contains two users named Admin1 and Admin2. All users are assigned a Microsoft 365 Enterprise E5 license and auditing is turned on.
You create the audit retention policy shown in the exhibit. (Click the Exhibit tab.)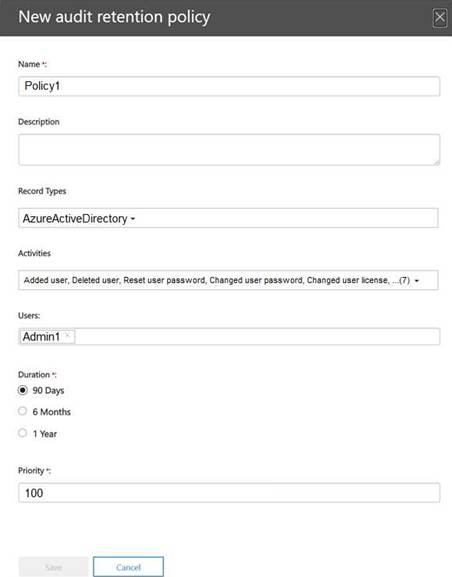
After Policy1 is created, the following actions are performed:  Admin1 creates a user named User1.
Admin1 creates a user named User1. Admin2 creates a user named User2.
Admin2 creates a user named User2.
How long will the audit events for the creation of User1 and User2 be retained? To answer, select the
appropriate options in the answer area.
NOTE: Each correct selection is worth one point.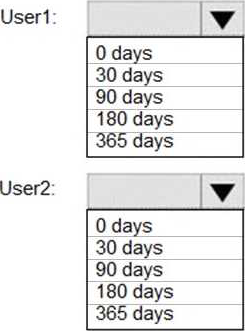
Solution:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/audit-log-retention-policies?view=o365-worldwide
Does this meet the goal?
Correct Answer:A