- (Exam Topic 1)
The process of attempting to exploit a weakness in a network after being given permission by the company is known as:
Correct Answer:A
- (Exam Topic 1)
A network technician is able to connect the switches between to offices, but the offices cannot communicate with each other, as each office uses a different IP addressing scheme. Which of the following devices needs to be installed between the switches to allow communication?
Correct Answer:C
- (Exam Topic 1)
A network technician is installing a new wireless network in a small office. Due to environment concerns, The customer wants the network to run exclusively on the %GHz frequency. Which of the following wireless technologies should the technician install meet this requirement? (Select TWO).
Correct Answer:AD
- (Exam Topic 2)
Please refer to the attached exhibit. Which of the following types of configuration management documentation is represented?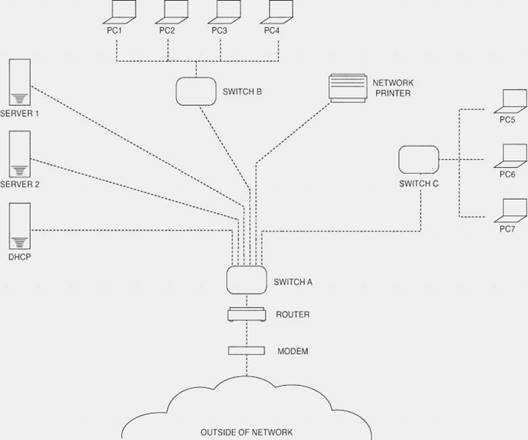
Correct Answer:C
- (Exam Topic 2)
Which of the following default ports would need to be open on a firewall to allow remote desktop access?
Correct Answer:C