A network administrator wants to set up redundant IPsec VPN tunnels on FortiGate by using two IPsec VPN tunnels and static routes.
*All traffic must be routed through the primary tunnel when both tunnels are up
*The secondary tunnel must be used only if the primary tunnel goes down
*In addition, FortiGate should be able to detect a dead tunnel to speed up tunnelfailover
Which two key configuration changes are needed on FortiGate to meet the design requirements? (Choose two,)
Correct Answer:A
Refer to the exhibit.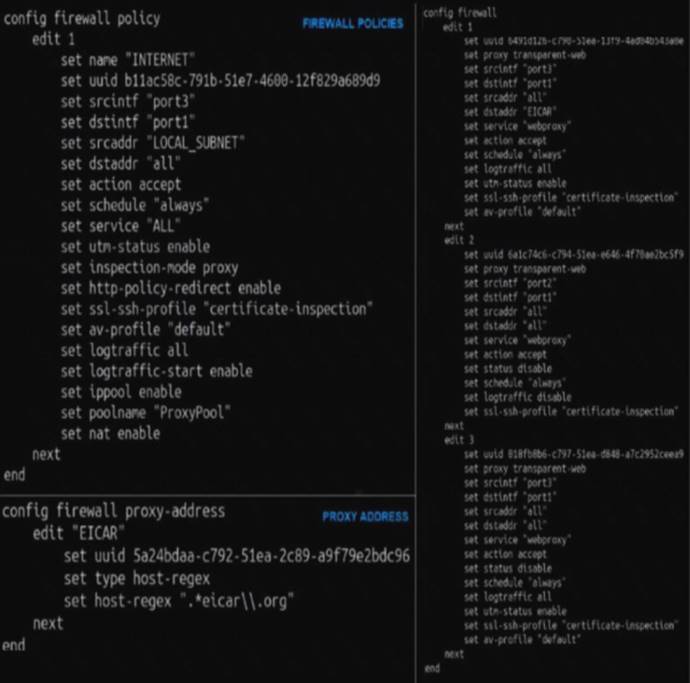
The exhibit shows a CLI output of firewall policies, proxy policies, and proxy addresses.
How does FortiGate process the traffic sent to http://www.fortinet.com?
Correct Answer:D
Examine the IPS sensor configuration shown in the exhibit, and then answer the question below.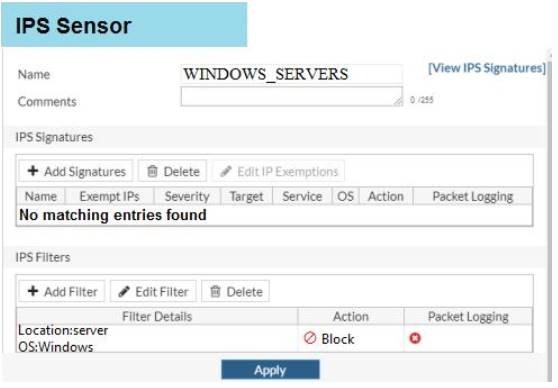
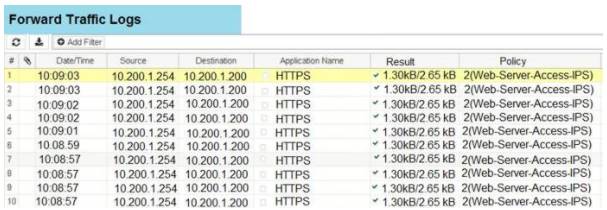
An administrator has configured the WINDOWS_SERVERS IPS sensor in an attempt to determine
whether the influx of HTTPS traffic is an attack attempt or not. After applying the IPS sensor, FortiGate is still not generating any IPS logs for the HTTPS traffic.
What is a possible reason for this?
Correct Answer:E
Refer to the exhibits to view the firewall policy (Exhibit A) and the antivirus profile (Exhibit B).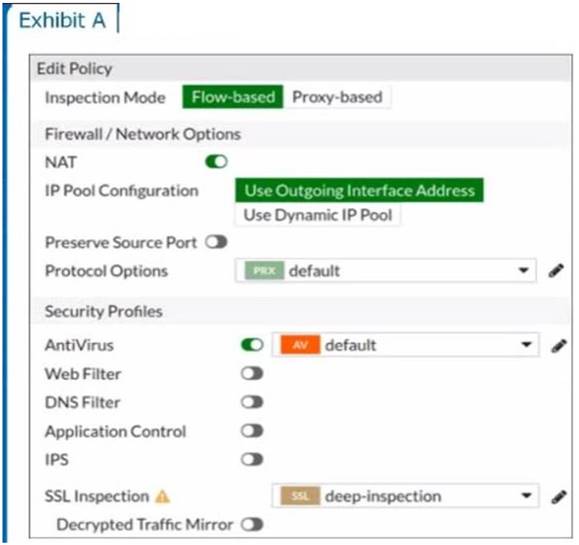
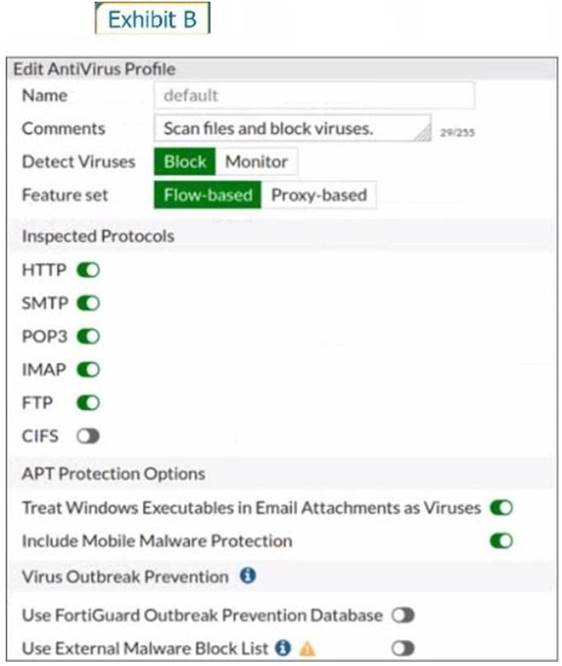
Which statement is correct if a user is unable to receive a block replacement message when downloading an infected file for the first time?
Correct Answer:A
Refer to the exhibit.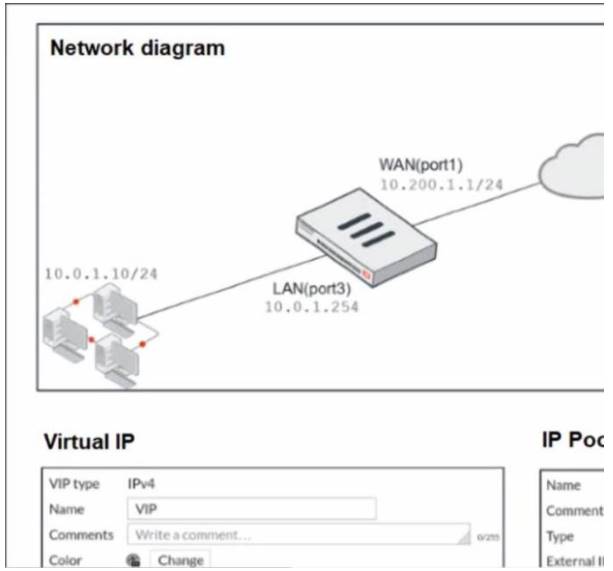
The exhibit contains a network diagram, virtual IP, IP pool, and firewall policies configuration. The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10 .0.1.254. /24. The first firewall policy has NAT enabled using IP Pool.
The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the internet traffic coming from a workstation with the IP address 10.0.1.10?
Correct Answer:A