What action does FortiClient anti-exploit detection take when it detects exploits?
Correct Answer:A
Which two statements are true about ZTNA? (Choose two.)
Correct Answer:AD
An administrator needs to connect FortiClient EMS as a fabric connector to FortiGate. What is the prerequisite to get FortiClient EMS to connect to FortiGate successfully?
Correct Answer:D
Which two statements are true about the ZTNA rule? (Choose two. )
Correct Answer:AD
"A ZTNA rule is a proxy policy used to enforce access control. ZTNA tags or tag groups can be defined to enforce zero trust role based access. Security profiles can be configured to protect this traffic."
"ZTNA rules help control access by defining users and ZTNA tags to perform user authentication and security posture checks. And just like firewall policies, you can control the source and destination addresses, and apply appropriate security profiles to scan the traffic."
https://docs.fortinet.com/document/fortigate/7.0.0/ztna-deployment/899992/configuring-ztna-rules-to-control-ac
Refer to the exhibits.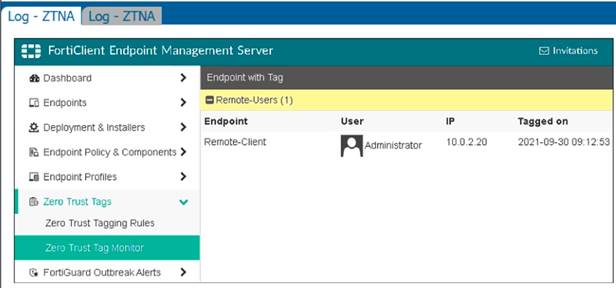
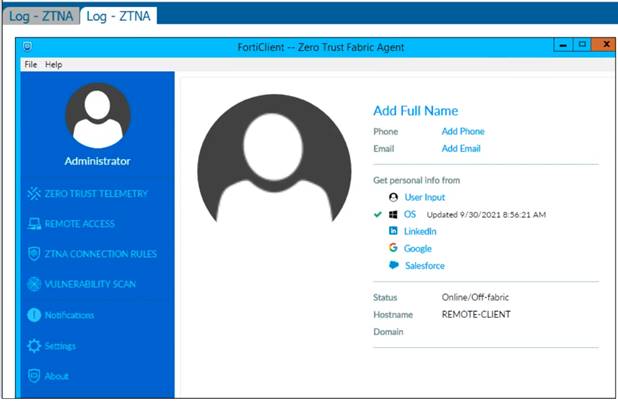
Which show the Zero Trust Tag Monitor and the FortiClient GUI status.
Remote-Client is tagged as Remote-Users on the FortiClient EMS Zero Trust Tag Monitor. What must an administrator do to show the tag on the FortiClient GUI?
Correct Answer:B