Which three methods of communication are used by FortiNAC to gather visibility information? (Choose three.)
Correct Answer:ACD
Which three Fortinet products can be used for device identification in an OT industrial control system (ICS)? (Choose three.)
Correct Answer:ADE
A. FortiNAC - FortiNAC is a network access control solution that provides visibility and control over network devices. It can identify devices, enforce access policies, and automate threat response.
* D. FortiSIEM - FortiSIEM is a security information and event management solution that can collect and analyze data from multiple sources, including network devices and servers. It can help identify potential security threats, as well as monitor compliance with security policies and regulations.
* E. FortiAnalyzer - FortiAnalyzer is a central logging and reporting solution that collects and analyzes data from multiple sources, including FortiNAC and FortiSIEM. It can provide insights into network activity and help identify anomalies or security threats.
Reference:
Fortinet NSE 7 - OT Security 6.4 Study Guide, Chapter 4: OT Security Devices, page 4-20.
An OT administrator is defining an incident notification policy using FortiSIEM and would like to configure the system with a notification policy. If an incident occurs, the administrator would like to be able to intervene and block an IP address or disable a user in Active Directory from FortiSIEM.
Which step must the administrator take to achieve this task?
Correct Answer:B
https://fusecommunity.fortinet.com/blogs/silviu/2022/04/12/fortisiempublishingscript
When you create a user or host profile, which three criteria can you use? (Choose three.)
Correct Answer:ADE
https://docs.fortinet.com/document/fortinac/9.2.0/administration-guide/15797/user-host-profiles
Refer to the exhibit, which shows a non-protected OT environment.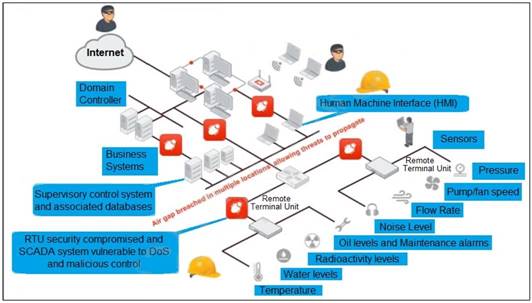
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
Correct Answer:ACD