No Installation Required, Instantly Prepare for the PAM-DEF exam and please click the below link to start the PAM-DEF Exam Simulator with a real PAM-DEF practice exam questions.
Use directly our on-line PAM-DEF exam dumps materials and try our Testing Engine to pass the PAM-DEF which is always updated.
Which of the following options is not set in the Master Policy?
Correct Answer:C
Password Complexity is not set in the Master Policy, but in the Platform Management settings for each platform. The Master Policy is a set of rules that define the security and compliance policy of privileged accounts in the organization, such as access workflows, password management, session monitoring, and auditing1. The Master Policy does not include any technical settings that determine how the system manages accounts on various platforms1. Password Complexity is a technical setting that defines the minimum requirements for the length and composition of the passwords that are generated by the CPM for the accounts associated with the platform2. Password Complexity can be configured in the Platform Management settings, which are independent of the Master Policy and can be customized according to the organization’s environment and security policies1.
The other options are set in the Master Policy, as follows:
✑ A. Password Expiration Time: This is a policy rule that determines how often passwords are changed. It can be set in the Master Policy under the Password Management section1.
✑ B. Enabling and Disabling of the Connection Through the PSM: This is a policy rule that determines whether users can connect to target systems through the PSM. It can be set in the Master Policy under the Session Management section1.
✑ D. The use of “One-Time-Passwords”: This is a policy rule that determines whether passwords are changed every time they are retrieved by a user. It can be set in the Master Policy under the Password Management section1. References:
✑ 1: The Master Policy
✑ 2: Platform Management, Password Complexity subsection
DRAG DROP
Match the log file name with the CyberArk Component that generates the log.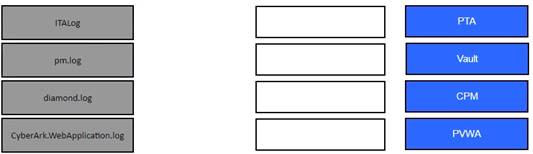
Solution:
References:
✑ Log Files
✑ [Defender PAM Sample Items Study Guide], Question 46, page 16
Does this meet the goal?
Correct Answer:A
Select the best practice for storing the Master CD.
Correct Answer:C
The best practice for storing the Master CD is to store it in a secure location, such as a physical safe. The Master CD contains the server key, the public recovery key, and the private recovery key, which are essential for starting, operating, and recovering the Vault. These keys are sensitive and should be protected from unauthorized access, loss, or damage. Therefore, storing the CD in a physical safe ensures that the keys are kept in a secure location when not in use, and that they are available when needed. This is the recommended option by CyberArk1.
The other options are not best practices and should be avoided, as they expose the keys to potential risks, such as theft, corruption, or deletion. Copying the files to the Vault server and discarding the CD is not secure, as it makes the keys accessible to anyone who can access the Vault server or compromise its security. Copying the contents of the CD to a Hardware Security Module (HSM) and discarding the CD is not feasible, as the HSM can only store the server key, not the recovery keys2. Storing the CD in a secure location, such as a physical safe, and copying the contents of the CD to a folder secured with NTFS permissions on the Vault is not necessary, as it creates redundant copies of the keys that may not be synchronized or updated. Moreover, NTFS permissions are not sufficient to protect the keys from malicious or accidental actions. References:
✑ Server Keys - CyberArk, section “Server Keys”
✑ Store the Server Key in an HSM - CyberArk, section “Store the Server Key in an HSM”
Which file must be edited on the Vault to configure it to send data to PTA?
Correct Answer:A
To configure the CyberArk Vault to send data to Privileged Threat Analytics (PTA), you must edit the dbparm.ini file on the Vault. This file contains parameters that specify how the Vault should forward syslog events to PTA, ensuring that the Vault can send secured syslog data to PTA for analysis and threat detection1. References:
✑ CyberArk Docs: Configure Vault Trusted Connection to PTA2
✑ Netenrich: CyberArk Vault via Syslog1
It is possible to restrict the time of day, or day of week that a [b]verify[/b] process can occur
Correct Answer:A
It is possible to restrict the time of day, or day of week that a verify process can occur by using the Verify Time Window parameter in thePlatform Management page. This parameter allows the administrator to define a time window for each platform, during which the verify process can be performed. The verify process will not run outside of this time window, unless it is manually initiated by the administrator. This feature can help reduce the load on the target systems and the network during peak hours. References:
✑ [Defender PAM Course], Module 4: Managing Accounts, Lesson 2: Account Verification, Slide 8: Verify Time Window
✑ [Defender PAM Documentation], Version 12.3, Administration Guide, Chapter 4: Managing Platforms, Section: Verify Time Window