Which core component is used to implement a Zero Trust architecture?
Correct Answer:C
Which network analysis tool can be used to record packet captures?
Correct Answer:B
Systems that allow for accelerated incident response through the execution of standardized and automated playbooks that work upon inputs from security technology and other data flows are known as what?
Correct Answer:C
Why is it important to protect East-West traffic within a private cloud?
Correct Answer:A
DRAG DROP
Match the description with the VPN technology.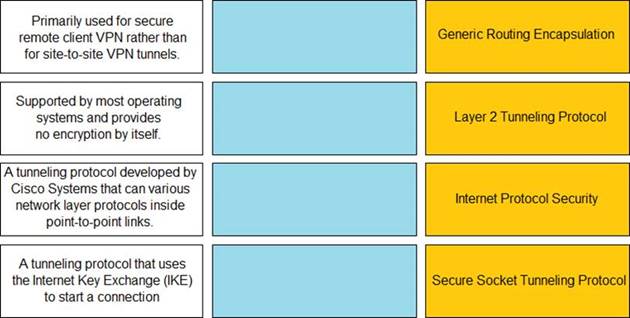
Solution: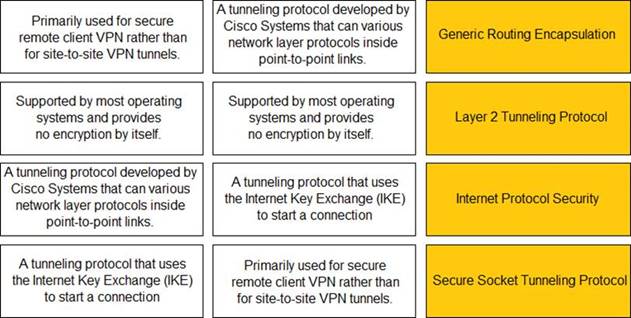
Does this meet the goal?
Correct Answer:A