Your company requires positive username attribution of every IP address used by wireless devices to support a new compliance requirement. You must collect IP –to-user mappings as soon as possible with minimal downtime and minimal configuration changes to the wireless devices themselves. The wireless devices are from various manufactures.
Given the scenario, choose the option for sending IP-to-user mappings to the NGFW.
Correct Answer:A
Which data-plane processor layer of the graphic shown provides uniform matching for spyware and vulnerability exploits on a Palo Alto Networks Firewall?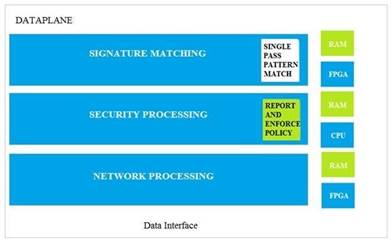
Correct Answer:A
Which two App-ID applications will need to be allowed to use Facebook- chat? (Choose two.)
Correct Answer:BC
Which type of security rule will match traffic between the Inside zone and Outside zone, within the Inside zone, and within the Outside zone?
Correct Answer:D