A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are: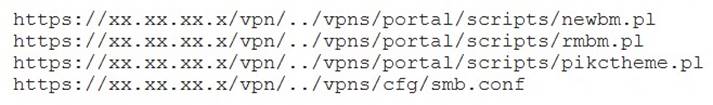
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
Correct Answer:C
A penetration tester has obtained root access to a Linux-based file server and would like to maintain persistence after reboot. Which of the following techniques would BEST support this objective?
Correct Answer:A
https://hosakacorp.net/p/systemd-user.html
Which of the following BEST describes why a client would hold a lessons-learned meeting with the penetration-testing team?
Correct Answer:C
When preparing for an engagement with an enterprise organization, which of the following is one of the MOST important items to develop fully prior to beginning the penetration testing activities?
Correct Answer:A
A company is concerned that its cloud VM is vulnerable to a cyberattack and proprietary data may be stolen. A penetration tester determines a vulnerability does exist and exploits the vulnerability by adding a fake VM instance to the IaaS component of the client's VM. Which of the following cloud attacks did the penetration tester MOST likely implement?
Correct Answer:A