During an engagement, a penetration tester found some weaknesses that were common
across the customer??s entire environment. The weaknesses included the following:
✑ Weaker password settings than the company standard
✑ Systems without the company's endpoint security software installed
✑ Operating systems that were not updated by the patch management system
Which of the following recommendations should the penetration tester provide to address the root issue?
Correct Answer:B
✑ Identified Weaknesses:
✑ Configuration Management System:
✑ Other Recommendations:
Pentest References:
✑ System Hardening: Ensuring all systems adhere to security baselines and configurations to reduce attack surfaces.
✑ Automation in Security: Using configuration management tools to automate security practices, ensuring compliance and reducing manual errors.
Implementing a configuration management system addresses the root issue by ensuring consistent security configurations, software deployments, and patch management across the entire environment.
=================
While performing an internal assessment, a tester uses the following command: crackmapexec smb 192.168.1.0/24 -u user.txt -p Summer123@
Which of the following is the main purpose of the command?
Correct Answer:C
The command crackmapexec smb 192.168.1.0/24 -u user.txt -p Summer123@ is used to perform password spraying on internal systems. CrackMapExec (CME) is a post- exploitation tool that helps automate the process of assessing large Active Directory
networks. It supports multiple protocols, including SMB, and can perform various actions like password spraying, command execution, and more.
✑ CrackMapExec:
✑ Command Breakdown:
✑ Password Spraying:
Pentest References:
✑ Password Spraying: An effective method for gaining initial access during penetration tests, particularly against organizations that have weak password policies or commonly used passwords.
✑ CrackMapExec: Widely used in penetration testing for its ability to automate and streamline the process of credential validation and exploitation across large networks.
By using the specified command, the tester performs a password spraying attack, attempting to log in with a common password across multiple usernames, identifying potential weak accounts.
=================
A penetration tester needs to help create a threat model of a custom application. Which of the following is the most likely framework the tester will use?
Correct Answer:D
The DREAD model is a risk assessment framework used to evaluate and prioritize the security risks of an application. It stands for Damage potential, Reproducibility, Exploitability, Affected users, and Discoverability.
✑ Understanding DREAD:
✑ Usage in Threat Modeling:
✑ Process:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
After a recent penetration test was conducted by the company's penetration testing team, a systems administrator notices the following in the logs:
2/10/2023 05:50AM C:usersmgraniteschtasks /query
2/10/2023 05:53AM C:usersmgraniteschtasks /CREATE /SC DAILY
Which of the following best explains the team's objective?
Correct Answer:D
The logs indicate that the penetration testing team??s objective was to create persistence in the network.
✑ Log Analysis:
✑ Persistence:
✑ Other Options:
Pentest References:
✑ Post-Exploitation: Establishing persistence is a key objective after gaining initial access to ensure continued access.
✑ Scheduled Tasks: Utilizing Windows Task Scheduler to run scripts or programs automatically at specified times as a method for maintaining access.
By creating scheduled tasks, the penetration testing team aims to establish persistence, ensuring they can retain access to the system over time.
=================
SIMULATION
You are a penetration tester running port scans on a server.
INSTRUCTIONS
Part 1: Given the output, construct the command that was used to generate this output from the available options.
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.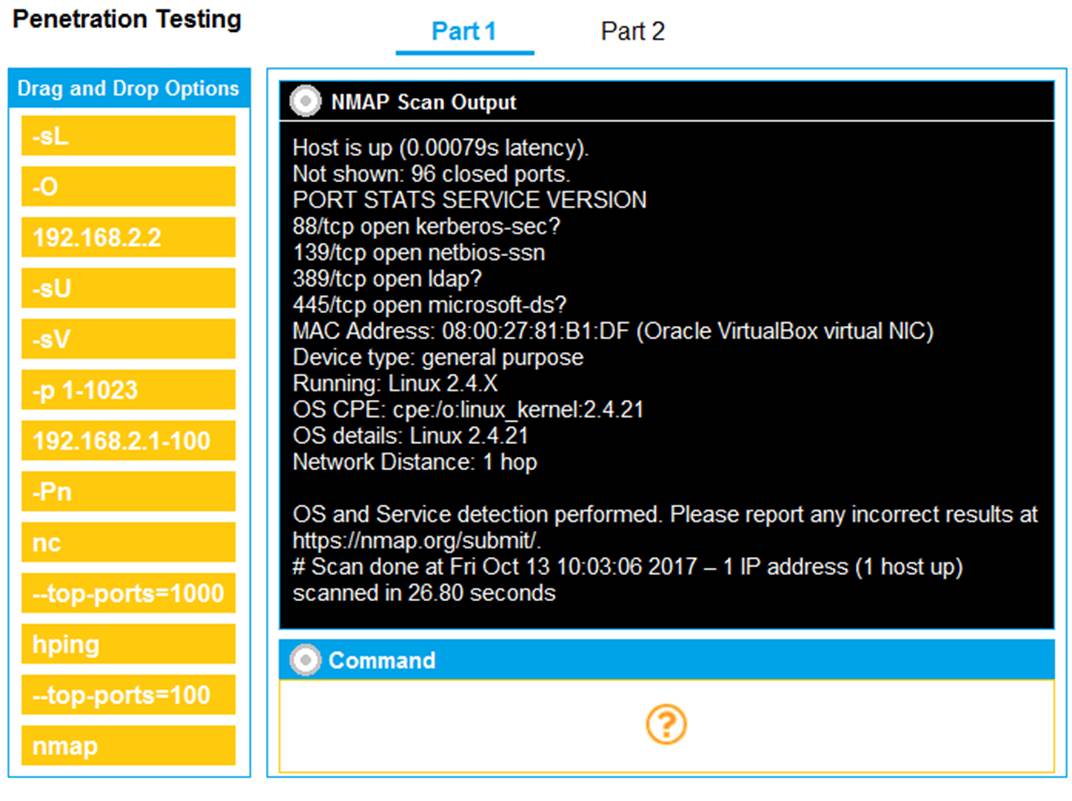
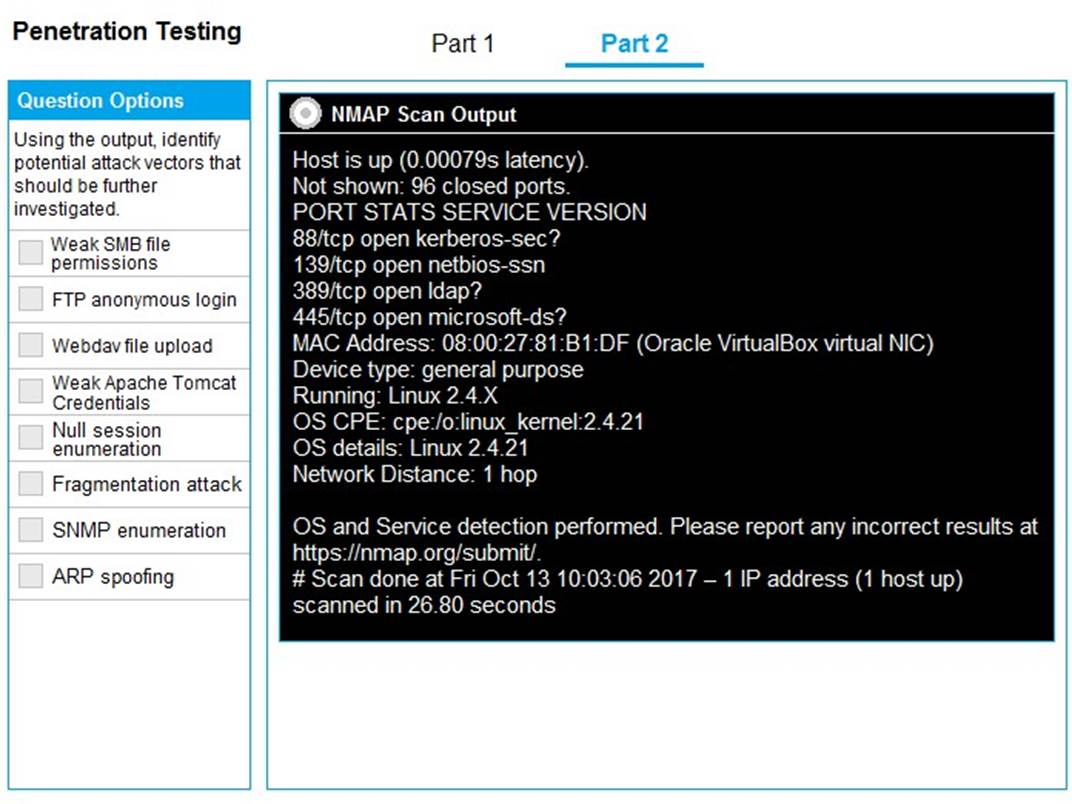
Solution:
Part 1 - 192.168.2.2 -O -sV --top-ports=100 and SMB vulns Part 2 - Weak SMB file permissions
https://subscription.packtpub.com/book/networking-and-
servers/9781786467454/1/ch01lvl1sec13/fingerprinting-os-and-services-running-on-a- target-host
Does this meet the goal?
Correct Answer:A