A security administrator is trying to determine whether a server is vulnerable to a range of attacks. After using a tool, the administrator obtains the following output: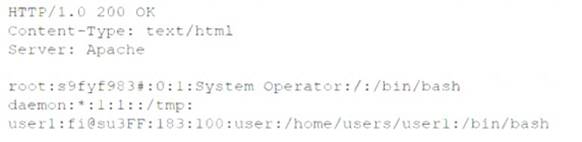
Which of the following attacks was successfully implemented based on the output?
Correct Answer:D
A nuclear plant was the victim of a recent attack, and all the networks were air gapped. A subsequent investigation revealed a worm as the source of the issue. Which of the following BEST explains what happened?
Correct Answer:A
The spread of misinformation surrounding the outbreak of a novel virus on election day ted to eligible voters choosing not to take the risk of going to the polls This is an example of:
Correct Answer:D
A network technician is installing a guest wireless network at a coffee shop. When a customer purchases an Item, the password for the wireless network is printed on the recent so the customer can log in. Which of the following will the technician MOST likely configure to provide the highest level of security with the least amount of overhead?
Correct Answer:A
An engineer wants to access sensitive data from a corporate-owned mobile device. Personal data is not allowed on the device. Which of the following MDM configurations must be considered when the engineer travels for business?
Correct Answer:D