A user contacts the help desk to report the following:
Two days ago, a pop-up browser window prompted the user for a name and password after connecting to the corporate wireless SSID. This had never happened before, but the user entered the information as requested.
The user was able to access the Internet but had trouble accessing the department share until the next day.
The user is now getting notifications from the bank about unauthorized transactions. Which of the following attack vectors was MOST likely used in this scenario?
Correct Answer:A
An attacker has successfully exfiltrated several non-salted password hashes from an online system. Given the logs below: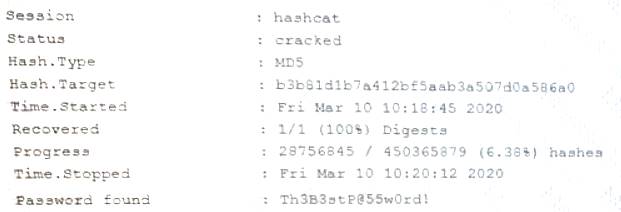
Which of the following BEST describes the type of password attack the attacker is performing?
Correct Answer:A
An attacker was easily able to log in to a company's security camera by performing a basic online search for a setup guide for that particular camera brand and model Which of the following BEST describes the configurations the attacker exploited?
Correct Answer:C
A network administrator needs to build out a new datacenter, with a focus on resiliency and uptime. Which of the following would BEST meet this objective? (Choose two.)
Correct Answer:AB
An analyst is trying to identify insecure services that are running on the internal network After performing a port scan the analyst identifies that a server has some insecure services enabled on default ports Which of the following BEST describes the services that are currently running and the secure alternatives for replacing them' (Select THREE)
Correct Answer:BCF