A security researcher has alerted an organization that its sensitive user data was found for sale on a website. Which of the following should the organization use to inform the affected parties?
Correct Answer:A
A network administrator is setting up wireless access points in all the conference rooms and wants to authenticate device using PKI. Which of the following should the administrator configure?
Correct Answer:C
The concept of connecting a user account across the systems of multiple enterprises is BEST known as:
Correct Answer:D
A security analyst is reviewing the following command-line output: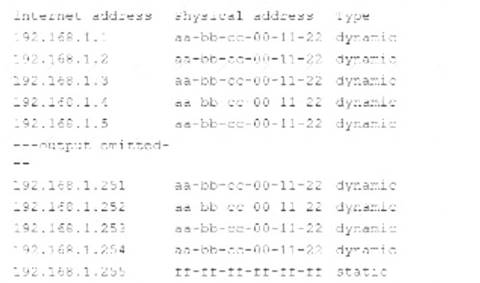
Which of the following Is the analyst observing?
Correct Answer:C
A security operations analyst is using the company's SIEM solution to correlate alerts. Which of the following stages of the incident response process is this an example of?
Correct Answer:C