- (Exam Topic 2)
A newly purchased corporate WAP needs to be configured in the MOST secure manner possible. INSTRUCTIONS
Please click on the below items on the network diagram and configure them accordingly:  WAP
WAP DHCP Server
DHCP Server  AAA Server
AAA Server Wireless Controller
Wireless Controller  LDAP Server
LDAP Server
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.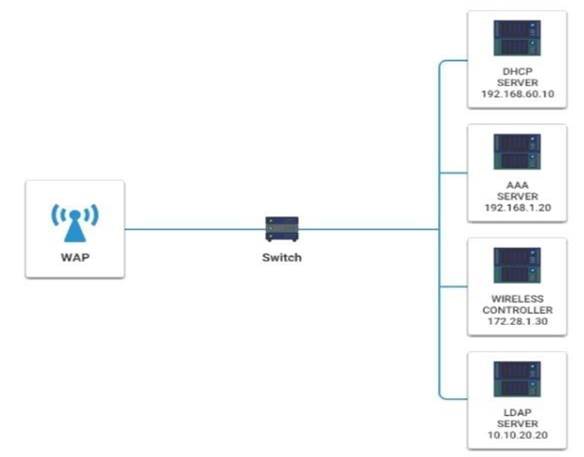
Solution:
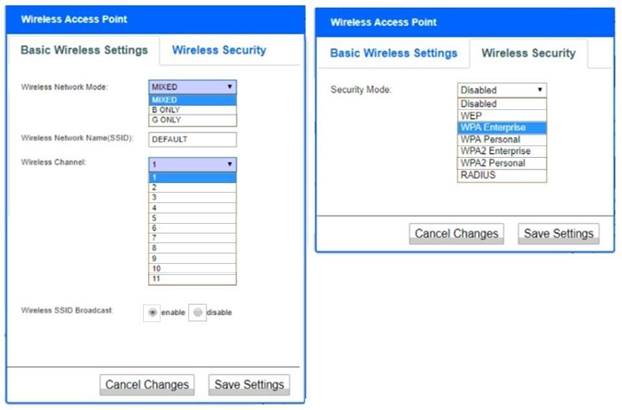
Wireless Access Point Network Mode – G only Wireless Channel – 11
Wireless SSID Broadcast – disable Security settings – WPA2 Professional
Does this meet the goal?
Correct Answer:A
- (Exam Topic 2)
Several universities are participating in a collaborative research project and need to share compute and storage resources. Which of the following cloud deployment strategies would best meet this need?
Correct Answer:A
A community cloud deployment strategy would best meet the need of several universities participating in a collaborative research project and needing to share compute and storage resources. A community cloud is a type of cloud service model that provides a shared platform for multiple organizations with common interests, goals, or requirements. A community cloud can offer benefits such as cost savings, scalability, security, privacy, compliance, and collaboration. References:
https://www.comptia.org/blog/cloud-service-models-saas-paas-and-iaas-explained https://www.certblaster.com/wp-content/uploads/2020/11/CompTIA-Security-SY0-601-Exam-Objectives-1.0.pd
- (Exam Topic 1)
During an incident, a company's CIRT determines it is necessary to observe the continued network-based transactions between a callback domain and the malware running on an enterprise PC. Which of the following techniques would be BEST to enable this activity while reducing the nsk of lateral spread and the risk that the adversary would notice any changes?
Correct Answer:C
Emulating the malware in a heavily monitored DMZ segment is the best option for observing network-based transactions between a callback domain and the malware running on an enterprise PC. This approach provides an isolated environment for the malware to run, reducing the risk of lateral spread and detection by the adversary. Additionally, the DMZ can be monitored closely to gather intelligence on the adversary's tactics and techniques. References: CompTIA Security+ Study Guide, page 129
- (Exam Topic 1)
Which of the following environments can be stood up in a short period of time, utilizes either dummy data or actual data, and is used to demonstrate and model system capabilities and functionality for a fixed,
agreed-upon duration of time?
Correct Answer:A
A proof of concept (PoC) environment can be stood up quickly and is used to demonstrate and model system capabilities and functionality for a fixed, agreed-upon duration of time. This environment can utilize either dummy data or actual data. References: CompTIA Security+ Certification Guide, Exam SY0-501
- (Exam Topic 2)
A web server log contains two million lines. A security analyst wants to obtain the next 500 lines starting from line 4,600. Which of the following commands will help the security analyst to achieve this objective?
Correct Answer:D
the cat command displays the contents of a file, the head command displays the first lines of a file, and the
tail command displays the last lines of a file. To display a specific number of lines from a file, you can use a
minus sign followed by a number as an option for head or tail. For example, head -10 will display the first 10 lines of a file.
To obtain the next 500 lines starting from line 4,600, you need to use both head and tail commands. https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/file-manipulation-tools/