- (Exam Topic 4)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to rt As a result, these questions will not appear in the review screen.
You have an Azure subscription named Sub1.
You have an Azure Storage account named Sa1 in a resource group named RG1.
Users and applications access the blob service and the file service in Sal by using several shared access signatures {SASs) and stored access policies.
You discover that unauthorized users accessed both the rile service and the blob service. You need to revoke all access to Sa1.
Solution: You regenerate the access keys. Does this meet the goal?
Correct Answer:A
To revoke a stored access policy, you can either delete it, or rename it by changing the signed identifier. Changing the signed identifier breaks the associations between any existing signatures and the stored access
policy. Deleting or renaming the stored access policy immediately effects all of the shared access signatures associated with it.
References:
https://docs.microsoft.com/en-us/rest/api/storageservices/Establishing-a-Stored-Access-Policy
- (Exam Topic 4)
You have an Azure subscription that contains the storage accounts shown in the following table.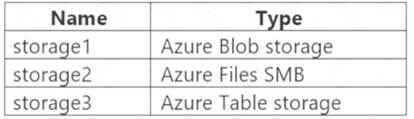
You need to configure authorization access.
Which authorization types can you use for each storage account? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Solution:
Graphical user interface, text, application, email Description automatically generated
Reference:
https://docs.microsoft.com/en-us/azure/storage/common/authorize-data-access
Does this meet the goal?
Correct Answer:A
- (Exam Topic 4)
You have an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains the users shown in the following table.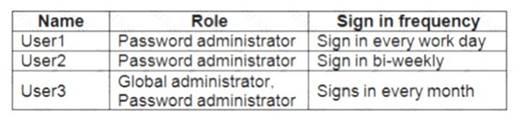
You configure an access review named Review1 as shown in the following exhibit.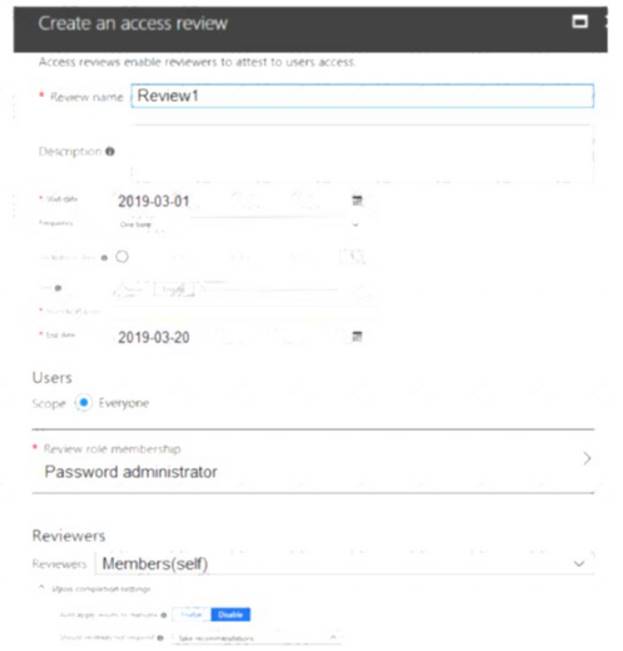
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.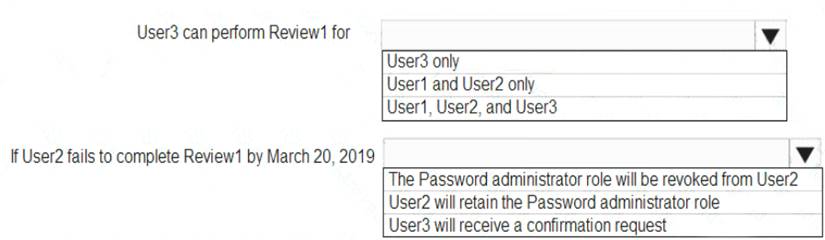
Solution:
Box 1: User3 only
Use the Members (self) option to have the users review their own role assignments. Box 2: User3 will receive a confirmation request
Use the Should reviewer not respond list to specify what happens for users that are not reviewed by the reviewer within the review period. This setting does not impact users who have been reviewed by the reviewers manually. If the final reviewer's decision is Deny, then the user's access will be removed.
No change - Leave user's access unchanged Remove access - Remove user's access Approve access - Approve user's access
Take recommendations - Take the system's recommendation on denying or approving the user's continued access
References:
https://docs.microsoft.com/bs-latn-ba/azure/active-directory/privileged-identity-management/pim-how-to-start-s
Does this meet the goal?
Correct Answer:A
- (Exam Topic 4)
You have an Azure subscription named Subscription1.
You deploy a Linux virtual machine named VM1 to Subscription1. You need to monitor the metrics and the logs of VM1. D18912E1457D5D1DDCBD40AB3BF70D5D
What should you use?
Correct Answer:A
- (Exam Topic 4)
You plan to connect several Windows servers to the WS11641655 Azure Log Analytics workspace.
You need to ensure that the events in the System event logs are collected automatically to the workspace after you connect the Windows servers.
To complete this task, sign in to the Azure portal and modify the Azure resources.
Solution:
Azure Monitor can collect events from the Windows event logs or Linux Syslog and performance counters that you specify for longer term analysis and reporting, and take action when a particular condition is detected. Follow these steps to configure collection of events from the Windows system log and Linux Syslog, and several common performance counters to start with.
Data collection from Windows VM
* 1. In the Azure portal, locate the WS11641655 Azure Log Analytics workspace then select Advanced settings.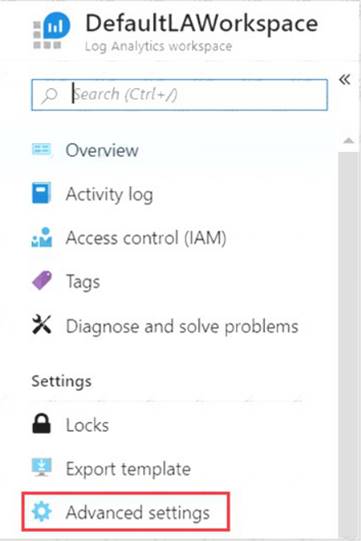
* 2. Select Data, and then select Windows Event Logs.
* 3. You add an event log by typing in the name of the log. Type System and then select the plus sign +.
* 4. In the table, check the severities Error and Warning. (for this question, select all severities to ensure that ALL logs are collected).
* 5. Select Save at the top of the page to save the configuration. Reference:
https://docs.microsoft.com/en-us/azure/azure-monitor/learn/quick-collect-azurevm
Does this meet the goal?
Correct Answer:A