- (Exam Topic 4)
You need to ensure that connections through an Azure Application Gateway named Homepage-AGW are inspected for malicious requests.
To complete this task, sign in to the Azure portal. You do not need to wait for the task to complete.
Solution:
You need to enable the Web Application Firewall on the Application Gateway.
In the Azure portal, type Application gateways in the search box, select Application gateways from the search results then select the gateway named Homepage-AGW. Alternatively, browse to Application Gateways in the left navigation pane.
In the properties of the application gateway, click on Web application firewall. For the Tier setting, select WAF V2.
In the Firewall status section, click the slider to switch to Enabled. In the Firewall mode section, click the slider to switch to Prevention. Click Save to save the changes.
Does this meet the goal?
Correct Answer:A
- (Exam Topic 3)
You plan to configure Azure Disk Encryption for VM4 Which key vault can you use to store the encryption key?
Correct Answer:A
The key vault needs to be in the same subscription and same region as the VM. VM4 is in West US. KeyVault1 is the only key vault in the same region as the VM. Reference:
https://docs.microsoft.com/en-us/azure/virtual-machines/windows/disk-encryption-key-vault
- (Exam Topic 4)
You have 15 Azure virtual machines in a resource group named RG1. All virtual machines run identical applications.
You need to prevent unauthorized applications and malware from running on the virtual machines. What should you do?
Correct Answer:B
Adaptive application control is an intelligent, automated end-to-end application whitelisting solution from Azure Security Center. It helps you control which applications can run on your Azure and non-Azure VMs (Windows and Linux), which, among other benefits, helps harden your VMs against malware. Security Center uses machine learning to analyze the applications running on your VMs and helps you apply the specific whitelisting rules using this intelligence.
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-adaptive-application
- (Exam Topic 4)
You have an Azure subscription that contains an Azure Sentinel workspace.
Azure Sentinel is configured to ingest logs from several Azure workloads. A third-party service management platform is used to manage incidents.
You need to identify which Azure Sentinel components to configure to meet the following requirements:  When Azure Sentinel identifies a threat, an incident must be created.
When Azure Sentinel identifies a threat, an incident must be created. A ticket must be logged in the service management platform when an incident is created in Azure Sentinel.
A ticket must be logged in the service management platform when an incident is created in Azure Sentinel.
Which component should you identify for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.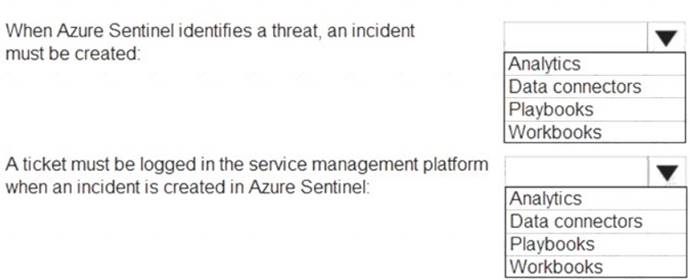
Solution:
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/create-incidents-from-alerts https://docs.microsoft.com/en-us/azure/sentinel/tutorial-respond-threats-playbook
Does this meet the goal?
Correct Answer:A
- (Exam Topic 4)
Your company uses Azure DevOps.
You need to recommend a method to validate whether the code meets the company’s quality standards and code review standards.
What should you recommend implementing in Azure DevOps?
Correct Answer:C
Branch policies help teams protect their important branches of development. Policies enforce your team's code quality and change management standards.
References:
https://docs.microsoft.com/en-us/azure/devops/repos/git/branch-policies?view=azuredevops& viewFallbackFrom=vsts